Remove 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ Email Bitcoin Virus
About 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ Bitcoin Email
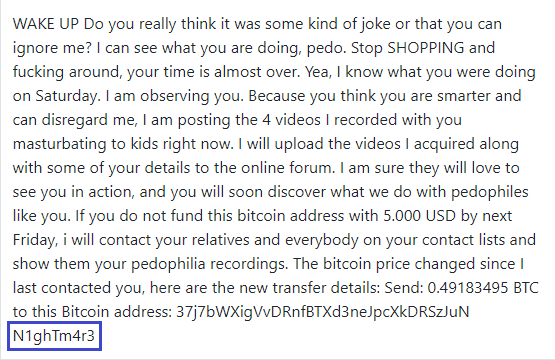
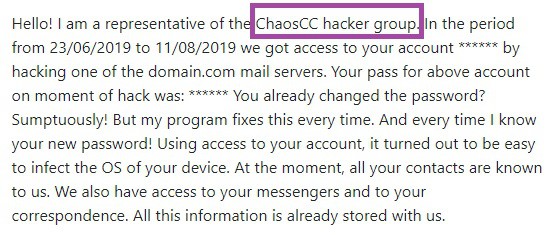
Some of our users reported a Bitcoin email scam that they have received, with the following message from the hacker:
Your computer was infected with my malware, RAT (Remote Administration Tool), your browser wasn’t updated / patched, in such case it’s enough to just visit some website where my iframe is placed to get automatically infected, if you want to find out more – Google: “Drive-by exploit”. My malware gave me full access and control over your computer, meaning, I got access to all your accounts (see password above) and I can see everything on your screen, turn on your camera or microphone and you won’t even notice about it. I collected all your private data and I RECORDED YOU (through your webcam) SATISFYING YOURSELF! After that I removed my malware to not leave any traces. I can send the video to all your contacts, post it on social network, publish it on the whole web, including the darknet, where the sick people are, I can publish all I found on your computer everywhere!
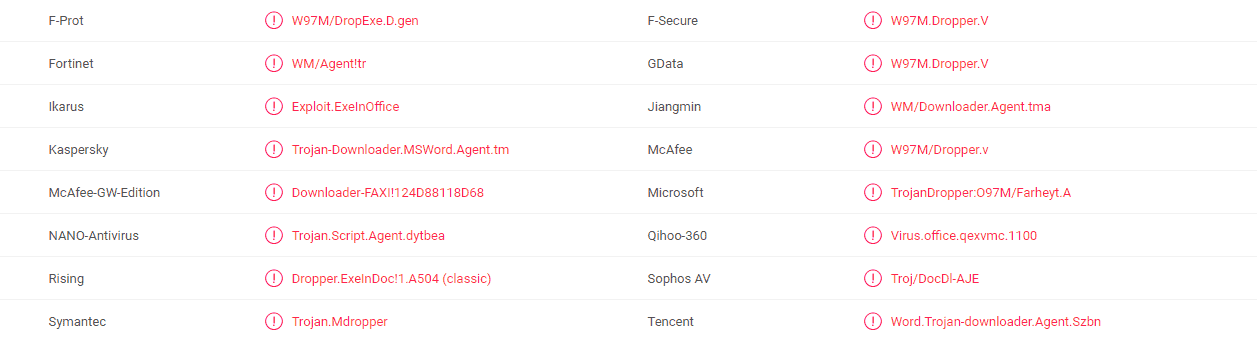
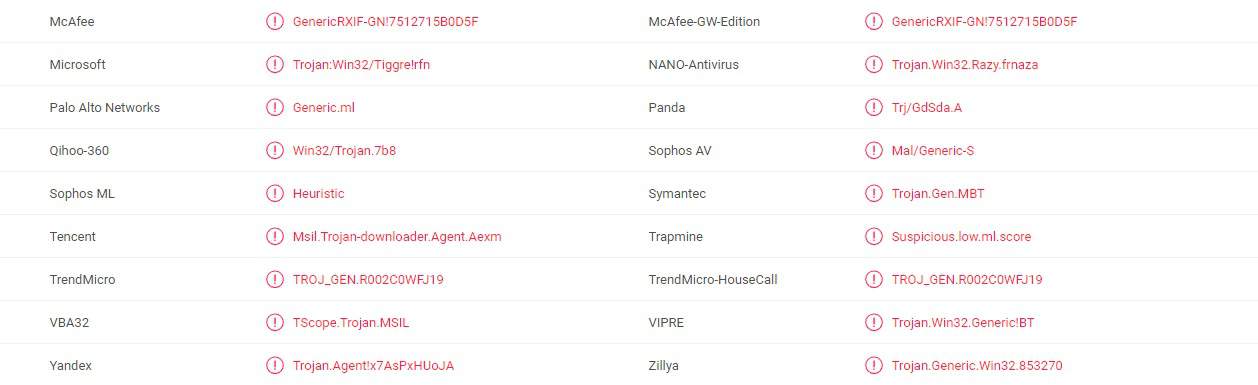
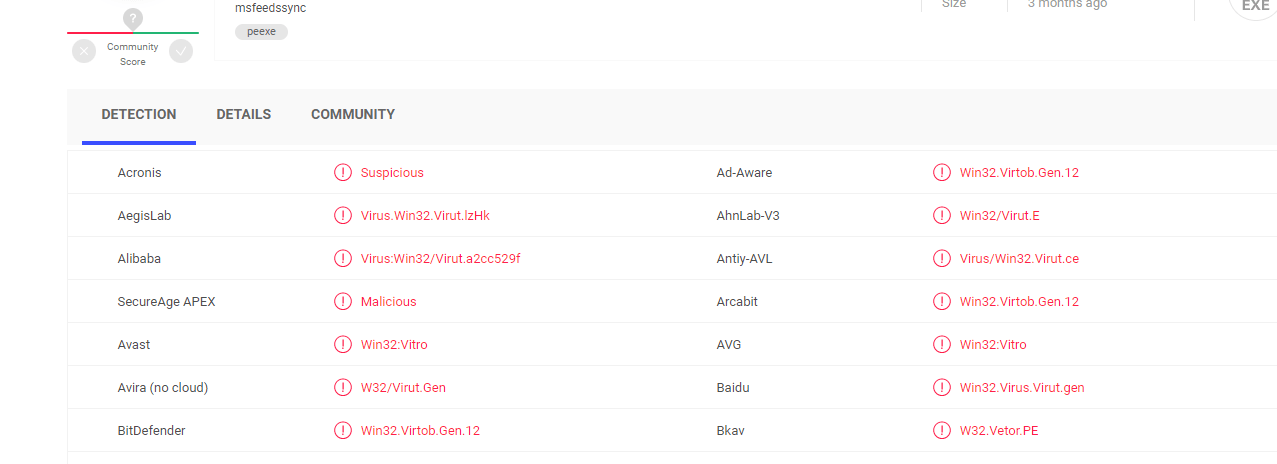
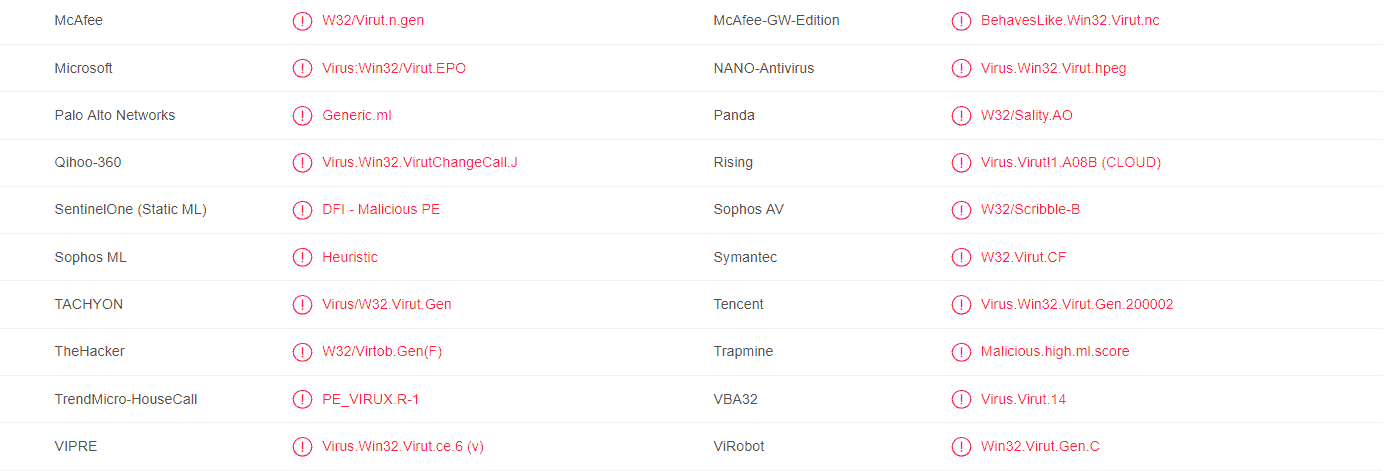
A majority of antivirus programs have detected the virus using 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ Bitcoin Wallet. You can see the attached report from VirusTotal below:
Protecting the safety of your computer system against the many forms of malware threats of the Internet is an essential and highly important part of owning a computer. A single malware infection with some nasty virus can cost you a lot of money, time and nerves and may result in loss of important data, software and more. All in all, it’s never a good thing if a malicious software program sneaks inside your computer. However, such things happen even to the most experienced, cautious and vigilant of computer users and this is when it is important to know how to counteract the infection that you have on your hands.
The first thing when you think that a malware has infected your machine is to determine the exact type of virus that you are going to be dealing with. Here, we will focus on a threat called 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ – if you suspect that this is the malicious program that has attacked your computer, then know that it is a representative of the Trojan Horse malware family. What this means is you must immediately take action in an attempt to remove the threat – the Trojans are among the most devastating threats and though they may not always have the same level of danger depending on the instance, there is no need to take any risks by allowing the infection to reside in your machine for any extended periods of time.
Characteristics of 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ – what we know so far
This insidious malware program is a rather new one and the security researchers are still gathering information about it. Currently, we do not know about its specific goal – the problem here is that the Trojan viruses like 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ , 1HB3KtKoguFuZ4BdmCv9Fc4tYTwDQgmqmW, Cve-2019-1663 tend to be quite versatile in their abilities and potential uses which makes it difficult to determine what they may be after in each separate case. In contrast to other threats like Ransomware, Rootkits, Spyware and so on which typically have some very specific uses and can’t really do anything beyond their initial task, a Trojan could be used as a metaphorical malware Swiss army knife meaning that the virus could carry out various criminal tasks and processes in the computer in an attempt to achieve different goals for its creators.
Some of the potential uses of 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ could be to steal sensitive personal and/or professional info from your machine and use that as the basis for blackmailing harassment, to damage your system and files, to remotely use your computer, turning it into another bot in its botnet, to spy on your activities online and offline, as well as many, many more.
Can I remove 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ Myself?
Considering all of the aforementioned points, your only choice is to act – act quickly and without hesitation towards removing the threat. We will offer you our help regarding this uneasy task in the form of the guide you will see below. To the guide, we have added a professional tool for malware removal which can be a very useful helper against this threat, especially if you use it in a combination with the manual steps from the guide.
SUMMARY:
| Name | 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | Some Trojans might trigger frequent errors or BSOD crashes as well as cause your PC to experience slow-downs due to the higher amounts of RAM and CPU that are being used by the malware program. |
| Distribution Method | Most users get Trojans by visiting shady and unsafe sites, by opening malicious spam e-mail attachments, by clicking on random web ads that are not safe and by downloading pirated software. |
Remove 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ Bitcoin Email Virus
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
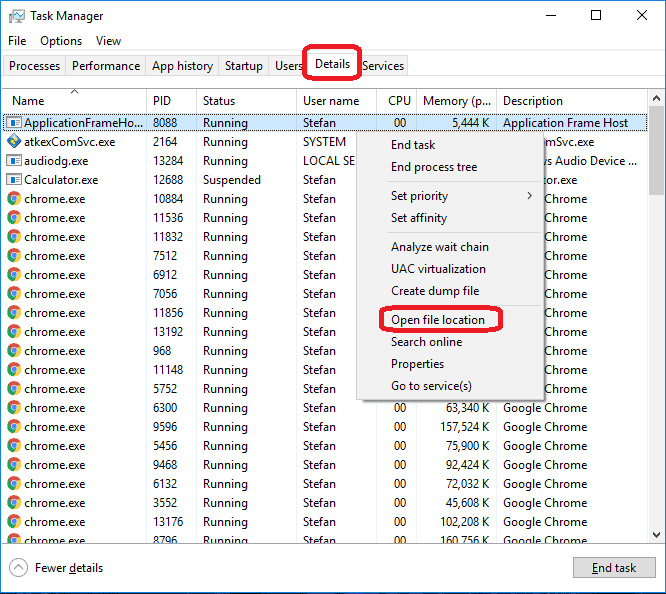
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:
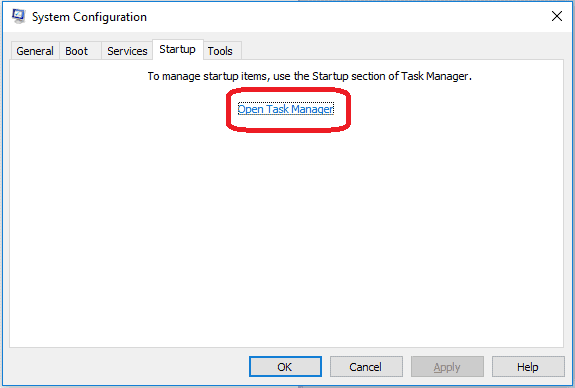
If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to 1LfYcbCsssB2niF3VWRBTVZFExzsweyPGQ. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.