[email protected] in depth
Ransomware programs seem to have flooded the online space in attempts to make money for their criminal developers. Thanks to their stealthy methods of distribution and the almost unnoticeable way they operate, those threats have become a lucrative “business” for various cyber criminals who seek a quick way to extort money from their victims. [email protected] is one of the latest representatives of this dreadful malware category and we’ve created this article to help the victims of this nasty cryptovirus effectively remove it from their systems and try to recover the files that it has encrypted.
When [email protected] gets into your PC (this can happen in so many ways), it begins to scan it for the presence of specific file formats. After having scanned the system in detail, the virus begins to create copies of each individual file with the only with difference between the originals and the copies being that the copies are locked by a complex encryption algorithm. The original files are deleted and the victims remain with a whole bunch of files that cannot be opened or used.
Can I Remove [email protected] myself?
If you are one of the unfortunate ones who have been greeted by a scary ransom-demanding notification on their screens which asks you to pay certain amount of money in order to regain the access to your most needed files, below, you will find a detailed removal guide and a trusted [email protected] removal tool, which may help you deal with the infection. You will also find a separate section with file-recovery suggestions which may eventually help you to restore your locked files from. We want to warn you, though, that it is not in all cases possible to recover files with those methods and sometimes it is quite likely to lose access to the mentioned files forever if there are no backup copies of your files on external devices and/or on online platforms. Nevertheless, we encourage you to give them a try instead of giving your money to some anonymous hackers. Before that, however, we advise you to familiarize yourself with the rest of the information contained in this article and safely remove [email protected] from the infected computer.
How Dangerous is [email protected]?
Ransomware threats like [email protected] , .Norvas , .Etols , [email protected] are some of the worst Internet threats today. Why? There are a number of reasons for this, the first one of which is the method they use to cause harm. The Ransomware-based infections are very different from other malicious programs because they use an essentially harmless process (the file-encryption) to harm their victims. What do we mean by this? The encryption process is a commonly used data-securing process that the vast majority of anti-virus programs will not flag as malicious. Therefore, even if you have installed a super strong and reliable antivirus in your system, the Ransomware will most likely not be stopped by it (unless the antivirus program has specialized Ransomware-detection features). In addition, the encryption that these types of programs use are often so tricky and complex that even specialists in this field may sometimes fail to decode them.
One very important thing worth considering if you intend to pay the ransom amount to the hackers in the hopes of saving your files. It is not uncommon that the decryption code sent by the criminals after the ransom payment does not work (or that no code gets sent whatsoever). This may be as a consequence of even the slightest error in it but there’s nothing you can do about it and, as you might have guessed, if this happens, there wouldn’t be any refunds!
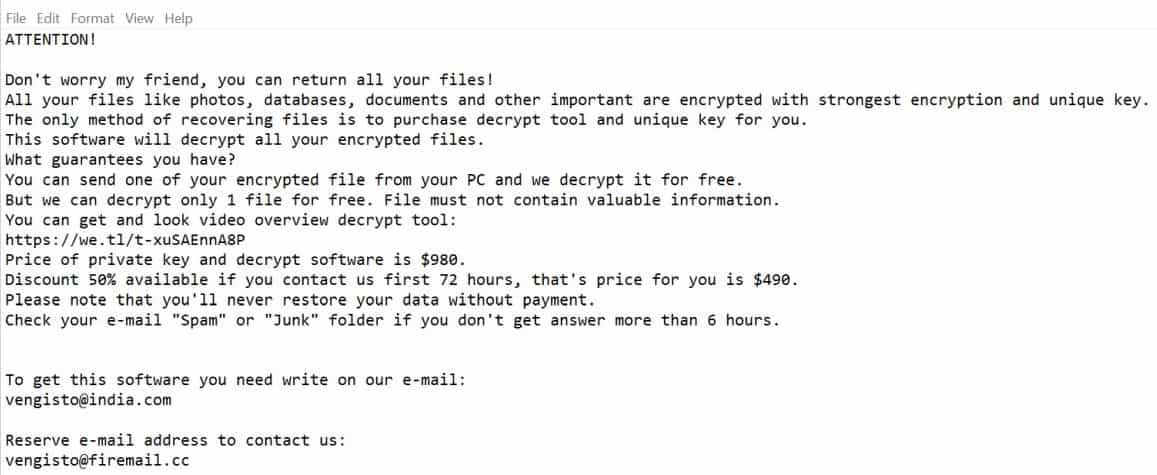
ATTENTION!
Don’t worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-vpovVceDWN
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
[email protected]Reserve e-mail address to contact us:
[email protected]
SUMMARY:
| Name | [email protected] |
| Type | Ransomware |
| Danger Level | High (Ransomware is by far the worst threat you can encounter) |
| Symptoms | Very few and unnoticeable ones before the ransom notification comes up. |
| Distribution Method | From fake ads and fake system requests to spam emails and contagious web pages. |
[add_third_banner]
Remove [email protected] Virus Ransomware
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to [email protected]
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the [email protected].
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and [email protected] , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – [email protected]
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to [email protected] Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
7: [email protected] Decryption
The previous steps were all aimed at removing the [email protected] Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them. For that, we have a separate article with detailed instructions on what you have to do in order to unlock your data. Here is a link to that guide.
Leave a Reply