About the [email protected] Email
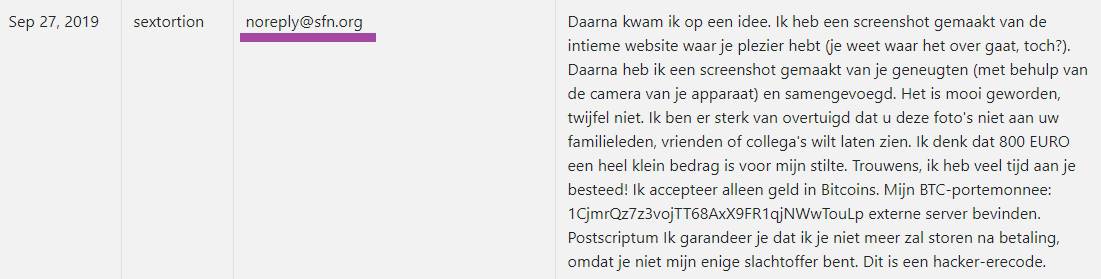
The details on this post will give you an idea about what precisely you should expect from a new Trojan Horse infection named [email protected]. This threat can be very sneaky, and dealing with it quickly, and effectively is of an utmost importance. But before you move right to the Removal Guide below, and its instructions, we will first cover the Trojans’ typical malicious capabilities, and their most popular infection techniques, as well as give you some helpful protective, and preventive tips. And, as you probably have come to this page not only to learn about the infection, but also to remove it, we’ve prepared detailed steps, and a trusted [email protected] removal tool for you in a guide down below. The instructions are intended to assist you with the manual detection and removal of [email protected] even if you are not an overly experienced user, but if you are dealing with a Trojan for the first time, the professional tool for quick automatic detection might be the more suitable removal option in your case, as it can take care of the infection automatically.
[email protected] – a multipurpose malware tool!
With the assistance of a Trojan like [email protected], the cyber criminals could easily perform various crimes. Some of the most prominent damaging actions that could be related to this form of malware may include spying, insertion of other dangerous pieces of malware such as Ransomware, and Spyware inside the computer, secret collection of personal information, file and software corruption, system destruction, and more. All in all, threats like [email protected], Chaos CC Hacker Group, “Hey I Know Your Password Is” are extremely dangerous, and you definitely don’t want them on your computer even for a minute. That’s why, as soon as you learn that you have been infected, you should remove them from your PC entirely.
If not, the concealed Trojan can launch various malicious processes, and seriously corrupt your files and software, and even cause irreparable damage to your entire system. Moreover, the hackers behind the infection may establish complete remote control over the infected computer, and secretly launch criminal processes such as spam distribution and virus insertion. They may even exploit the RAM and the CPU resources for activities like cryptocurrency mining, and involve your computer in various cyber crimes without your awareness. That’s why you should remove [email protected] instantly, as soon as you detect it on your system. This way, you will prevent the hackers from setting up their control over your computer and messing with it as they please.
How can you prevent Trojans from infecting your PC?
We will not say anything new here, but the best way of dealing with Trojans that you can have is preventing their attack in the first place. Installing a reputable security software on your PC, for instance, could be a very good investment in your virtual security. Such software is invaluable when it comes to detecting threats that hide their symptoms like [email protected]. Moreover, a good antivirus program can detect, and notify you about the concealed malicious code before it has succeeded in causing harm. However, don’t overlook that fact that malware is evolving every day, which is why you should frequently update your virus definitions in order to provide your system with adequate protection against new threats.
SUMMARY:
| Name | [email protected] |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | This threat rarely shows visible symptoms but if you notice some unusual system activity, you should run a system scan. |
| Distribution Method | Software bundles, torrents, illegal websites, spam messages, malicious email attachments. |
[add_third_banner]
Remove [email protected] Email
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to [email protected]
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the [email protected].
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and [email protected] , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – [email protected]
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to [email protected]. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
Leave a Reply