If you have been infected by a Trojan Horse called N1ght m4re, then the following article is exactly what you need in order to deal with this stealthy infection. Trojans are among the most dangerous malware types that you may encounter on the web and they are also among the most widespread. Nearly three in every four malware infections are typically caused by representatives of this exact category. This also explains why the Trojans are well-known even to people who are less tech-savvy. However, despite being so widespread, most users still don’t know how to protect their systems from threats like N1ght m4re, what to expect from them and how to remove them. That’s why it might have come to you like a shock when you discovered the N1ght m4re infection inside your computer. On this page, however, we will provide you with all the information that you need to know about this Trojan, as well as a detailed removal guide and a professional removal tool for automatic virus detection.
What are Trojans like N1ght m4re Email?
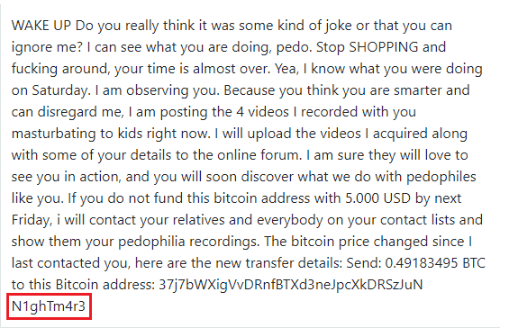
A Trojan (like the one you are currently dealing with) can have almost unlimited abilities of causing damage to your system. This is one of the main reasons why such viruses are the malware of choice for many cyber criminals. Besides, threats like N1ght m4re are incredibly stealthy and can remain hidden deep inside your system for an indefinite period of time. The worst is, they may not show even the slightest symptoms, which makes their detection and removal a real challenge, especially if you don’t have reliable security software at hand.
Another characteristic trait that makes the Trojans so feared is the fact that there is no way of knowing what exactly those threats may do while hiding inside your computer.
Perhaps topping the list of most common uses would be theft. An infection like N1ght m4re is the perfect tool for theft of personal information, important files, confidential documentation, login credentials, and even banking details. The malware can secretly collect different types of data and transmit it back to the hackers without you knowing about it. If the Trojan is a more sophisticated piece of malicious programming, it may compromise your computer in such a way that it may provide full remote access to the attackers. That way, they will be able to do everything they want inside the system, including replacing, corrupting, deleting, and modify different system processes and tasks, and even installing other malware such as Ransomware, Spyware or Viruses in your machine. There are plenty of other possible ways in which a Trojan can attack you. Resource exploitation, malware distribution, destruction, spamming – you name it.
Therefore, if you have N1ght m4re on your system, you have two very important tasks. The first is, obviously, to remove the infection. You can do this manually, with the help of the removal guide below, or you can use the professional removal tool instead. The second task you have is to eliminate any weaknesses your system has in order to prevent online threats from sneaking inside your computer. For that we suggest you update your current security software to the latest version, or invest in a reliable antivirus program for long-term protection in case you currently don’t have such software.
N1ght m4re SUMMARY:
| Name | N1ght m4re |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | Trojans are very stealthy threats which rarely show visible symptoms of their presence. |
| Distribution Method | Spam, malicious email attachments, cracked software, infected ads, misleading links, illegal websites. |
[add_third_banner]
Remove N1ght m4re Email Hacker Scam
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to N1ght m4re
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the N1ght m4re.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and N1ght m4re , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – N1ght m4re
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to N1ght m4re Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
Leave a Reply