Remove 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L Bitcoin Email Virus
About 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L Bitcoin Email
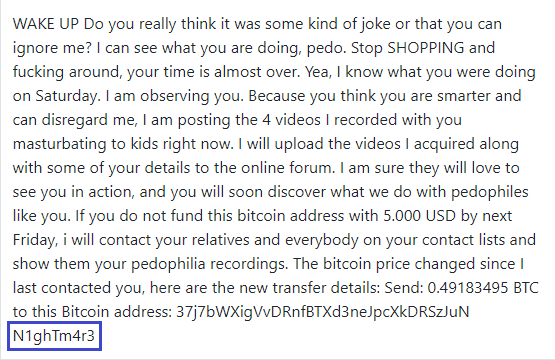
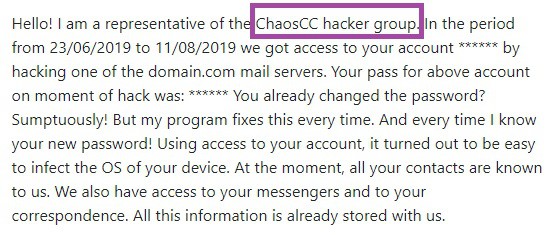
Some of our users reported an email scam that they have received, with the following message:
こんにちは! あなたは私を知らないかもしれませんし、なぜあなたはこの電子メールを受け取っているのだろうと思っていますか? この瞬間、私はあなたのアカウントをハッキングし、そこからメールを送りました。 私はあなたのデバイスに完全にアクセスできます! 今私はあなたのアカウントにアクセスできます! まあ、私は$990が私たちの小さな秘密の公正な価格だと信じています。 あなたはBitcoinによる支払いを行います(これはわからない場合は、Googleの「ビットコインの購入方法」を検索してください)。 私のBTC住所: 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L (それはcAsEに敏感なので、コピーして貼り付けてください) 注意: お支払いを行うには2日以内です。 (この電子メールメッセージには特定のピクセルがあり、この瞬間にこの電子メールメッセージを読んだことがわかります)。 私がBitCoinを手に入れなければ、私は間違いなく、家族や同僚などあなたのすべての連絡先にビデオ録画を送ります。 しかし、私が支払いを受けると、すぐにビデオを破壊します。 これは非交渉可能なオファーですので、このメールメッセージに返信して私の個人的な時間を無駄にしないでください。 次回は注意してください!より良いウイルス対策ソフトウェアを使用してください! さようなら!
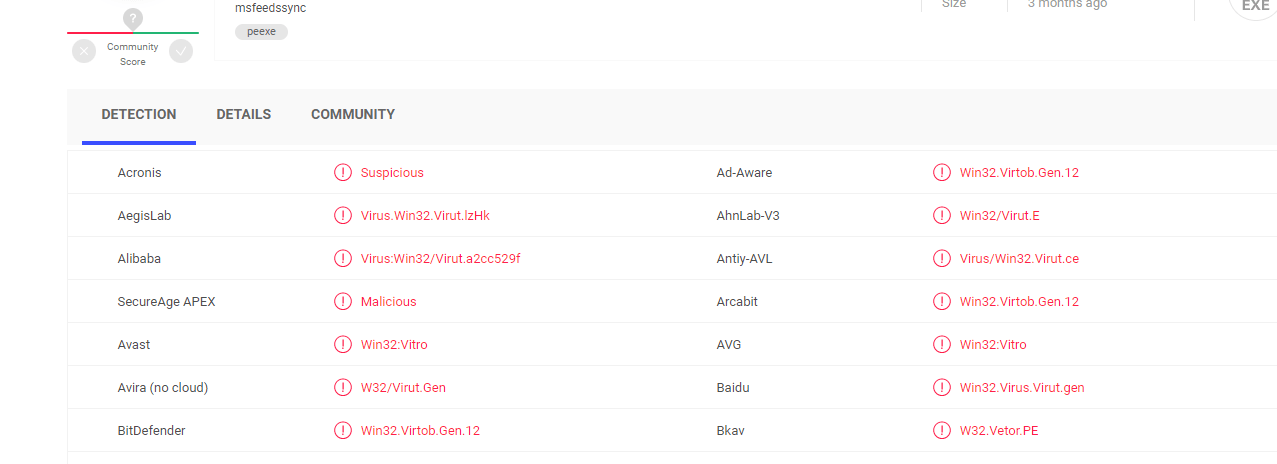
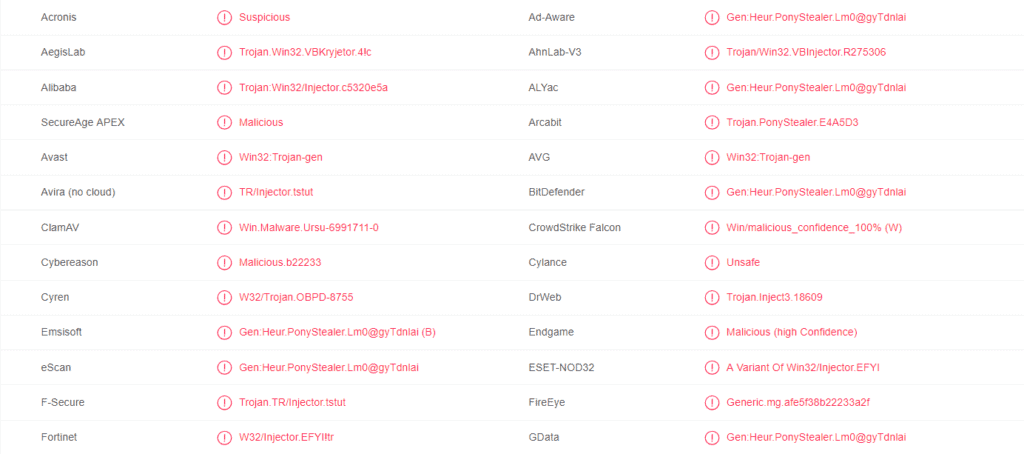
A Trojan (or a Trojan Horse) is a very malicious computer program, created by cyber criminals, the purpose of which is to secretly infect a given computer system and to launch certain harmful activities on it which will result in system damage, theft of information, security holes and other unpleasant effects. The reason we are saying this is because recently, there are some extremely dangerous pieces of malware (1HB3KtKoguFuZ4BdmCv9Fc4tYTwDQgmqmW, Cve-2019-1663) roaming around the web and spreading via scams, phishing emails, spam messages and infected attachments. One such infection is the Trojan-based piece of malware called 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L Bitcoin Wallet which has the ability to spy on you without your knowledge, steal personal data and use it against you or provide remote access to various hackers among other activities.
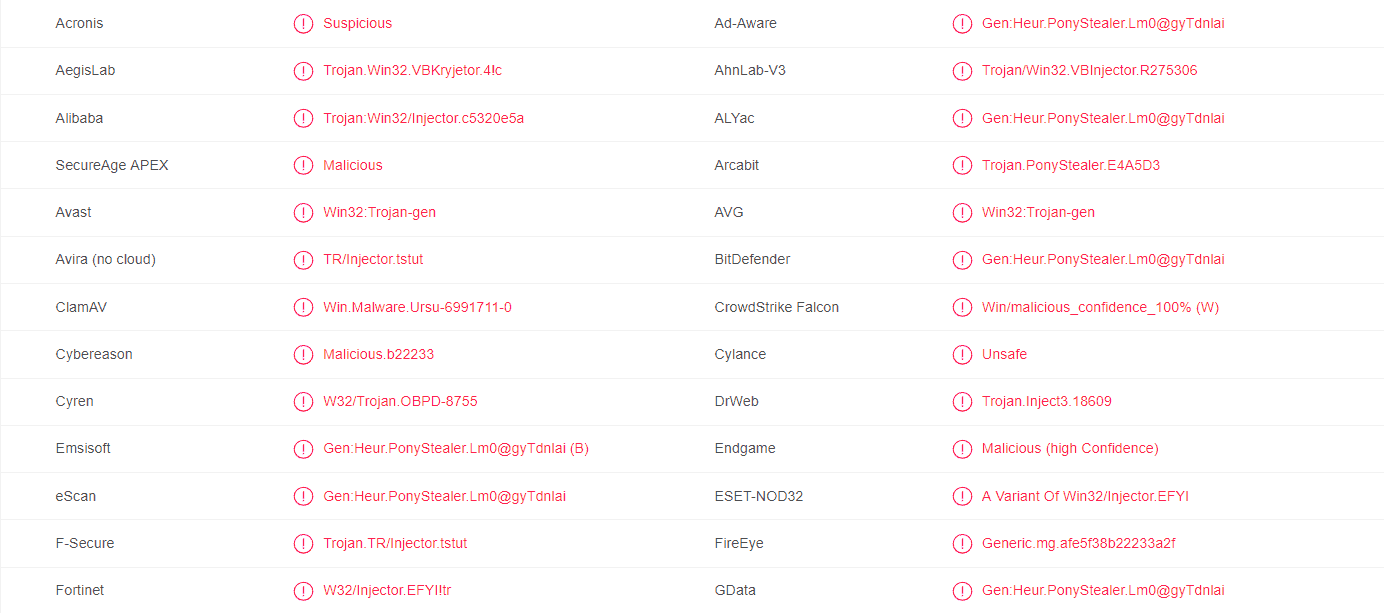
Usually, the most common criminal deeds that such programs could relate to are linked to banking frauds and theft of financial information, credit or debit card details, misuse of personal information, espionage, Ransomware distribution, as well as system and data corruption and destruction. In many cases, an infection with a Trojan may provide different hackers with unauthorized remote access to the compromised machine and let them take control over its resources. Unfortunately, the effects of the attack don’t always come immediately after you have been infected because, usually, once the Trojan enters the system, it nests deep into the OS and hides all of its traces for an indefinite period of time. This allows it to secretly launch its malicious agenda without being detected in a moment when nobody is expecting it. This being said, a Trojan Horse infection is much more complex and stealthy than a regular computer virus, therefore, it is much more difficult to detect and remove it.
Can I Remove 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L myself?
On this page, however, there is a special removal guide which explains how to remove one particularly nasty Trojan-based threat called 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L. If you are reading this because 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L has somehow nested inside your PC or you have a doubt that such a Trojan might be lying dormant in the background, the instructions below will help you carefully check your entire PC for malicious files and delete any potentially dangerous program.
Since the activities of each Trojan very much depend on the intentions of its criminal creators, we can’t really tell you what kind of a damage a threat like 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L may cause if not removed. What we can tell you for sure, though, is that nothing good expects you if a representative of this malware category has access to your machine. That’s why it is best to run a full scan with a professional removal tool such as the one that you will find below and carefully delete anything that is detected as a threat to your PC.
Unfortunately, most Trojans, including 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L, find their way inside the people’s machines accidentally, when the users interact with sketchy web content, infected links, ads, and cracked software installers. The most common way to invite a malware of this type on your computer is to download different free program keys, cracked installation packs, free illegal music or movies, games or torrents, from an unknown source. Once you click on the carrier, the Trojan is silently installed in the system. That’s why it is so important that you stick to reliable sources and keep away from unfamiliar web locations or shady downloads when downloading and installing new programs or surfing the web. And of course, invest in professional software for computer protection which can detect and remove potential threats on time.
SUMMARY:
| Name | 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L |
| Type | Trojan |
| Danger Level | High (18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L Trojans are often used as a backdoor for Ransomware) |
| Symptoms | 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L Some Trojans might trigger frequent errors or BSOD crashes as well as cause your PC to experience slow-downs due to the higher amounts of RAM and CPU that are being used by the malware program. |
| Distribution Method | Most users get Trojans by visiting shady and unsafe sites, by opening malicious spam e-mail attachments, by clicking on random web ads that are not safe and by downloading pirated software. |
Remove 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L Bitcoin Email Virus
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
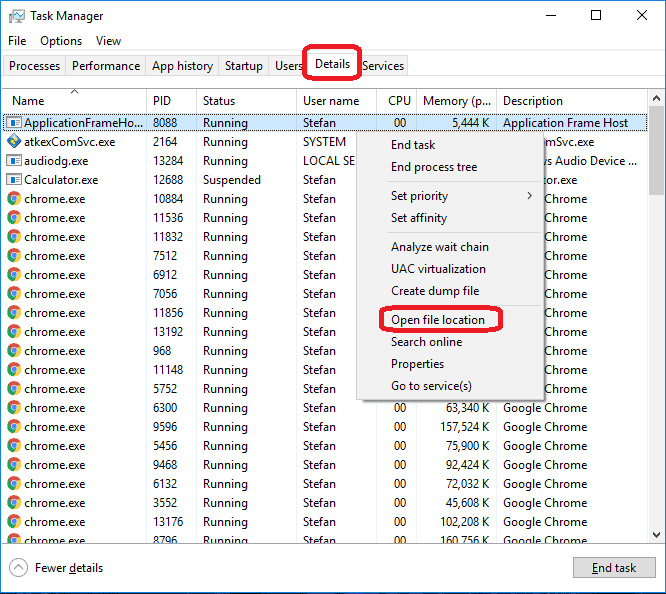
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:
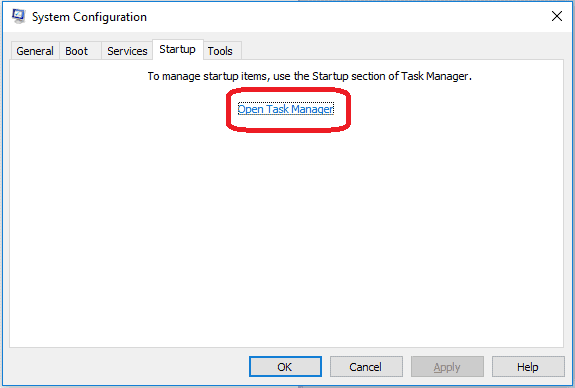
If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to 18BJwpv2RVfCZQP2D4WaduZwef7sXFwP4L Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.