Remove DataTransportation “Malware” (Mac Guide)

The applications from the browser hijacker category are commonly regarded as potentially unwanted pieces of software even though they lack the harmfulness of commonly encountered computer threats such as Ransomware, Trojans and other viruses. This is quite understandable because these applications have the ability to fill the users’ browsers with aggressive advertisements in the forms of ads, pop-ups, banners, colorful offers, redirect links, etc., which could only be removed if the hijacker gets eliminated completely. They typically take over popular browsing programs and their most common targets are Safari, Chrome and Firefox. After entering the browser, the hijackers install some new sponsored components (search engines, toolbar buttons, homepage URLs, etc.) inside of it without asking for approval. These are the main reasons why most people who come to experience the effects a browser hijacker may have on their browser are so eager to uninstall the pesky software and remove the obstructive ads and browser changes that come with it.
Unfortunately, a major problem with these applications is that their successful detection and elimination is oftentimes a bit tricky. Most of the users face difficulties when trying to uninstall the browser hijacker because, unlike regular programs and apps which have built-in uninstallation option, this type of software typically doesn’t have an uninstallation kit or menu. Removing the application from the browser’s extensions manager or changing the browser is also not a solution because the hijacker can usually re-add itself on any browser the very next time you start a new browsing session if its files aren’t meticulously removed from the system. That’s why one of the most effective elimination methods is through the use an automatic removal tool. Another good removal option is the using a specialized removal guide for uninstalling this specific app. If you are already having issues with unwanted page-redirects, strange browser changes and ads, the source of which is an application called DataTransportation, then, the instructions in the removal guide below and the removal tool linked there can help you to deal with this particular browser hijacker in a fast and reliable manner.
If you have given a quick glance at the instructions above, you probably have understood that the removal process of DataTransportation requires to do quite a lot of things before you can be sure the hijacker is removed. Still, if you repeat the instructions accurately, you should be able to get rid of the browser hijacker without any problem. After all, this is not some nasty virus or a sneaky malware program such as Ransomware or Spyware, which can hide inside your system and remain unnoticed. Furthermore, a professional removal tool such as the one on this page can also easily detect DataTransportation and remove it.
Fortunately, the hijacker is unlikely to engage in any criminal or harmful activities, however, this is not an application that should be tolerated for too long. Its ads and its random page-redirects may originate from questionable sources and you may have no control over their generation. What is more, the sponsored messages that may get displayed on your screen with the help of this application may trick you into purchasing some low-quality products or services or may land you on unfamiliar websites full of sketchy content. For this reason, it is simply better to eliminate the risks of an accidental encounter with questionable ads and security hazards and regain control over your favorite browser.
SUMMARY:
| Name | DataTransportation |
| Type | Browser Hijacker |
| Danger Level | Medium (nowhere near threats like Ransomware, but still a security risk) |
| Symptoms | A search engine replacement or a change in the homepage url may be initiated by this program. |
| Distribution Method | Software bundling and spam messages are common methods for distribution of this program. |
Remove DataTransportation “Malware”
Step 1: Closing Safari (or any other browser that you may be using at the moment)
First, you will need to close your browser if it is still open. If you can’t do that normally, you will need to Force Quit it:
Open the Apple Menu and select Force Quit to do that. You can also use the ⌘ key + Option Key combination to open the Force Quit Applications dialog box. In this box, select the Safari browser (or whatever browser you are using) and then click on the Quit button. Confirm the action by selecting Force Quit again.
Step 2: Killing suspicious processes
Ope Finder and go to Applications > Utilities and then open Activity Monitor. Now take a careful look at the processes there – look for any that seem suspicious, unknown and questionable. If you think that a given process may be the culprit behind the issue or may at least be related to it, highlight it with the mouse and select the i option at its top.
In the box that opens, click on Sample.
Scan the sample files with the online scanner we have on this page and if any of them get flagged as malicious, delete them and then kill their processes.
Step 3: Safely launching the browser
Hold the Shift from your keyboard and then launch Safari – holding Shift will prevent any previously opened pages to load again, just in case any of them were related to the problem.
If any problematic pages still load after you safe-launch the browser, then do the following:
Force-Quit the browser (Safari) again and then turn off your Wi-Fi connection by clicking on the Wi-Fi off option from the Mac Menu. If you are using cable Internet, simply disconnect the cable from your Mac.
Step 4: Uninstalling suspicious extensions
After you safe-launch Safari and are sure none of the previously opened pages load now, go to Preferences > Extensions.
Select and uninstall (by clicking on the Uninstall button) all extensions there that are unfamiliar to you or that you think may be suspicious. If you are not sure about a certain extension, it’s better to uninstall it – no extension is required for the normal functioning of the browser.
Step 5: Cleaning Safari
If you have other browsers aside from Safari, do the following:
In Safari, open Preferences from the browser’s menu and go to Privacy.
Select Remove All Website Data and then Remove Now. Note that this will delete all stored site data including any saved passwords and usernames. In other words, you will have to manually log-in to every site where you have a registration so make sure you remember your usernames and passwords.
Back in Preferences, click on General and see what your Safari’s homepage is. If it has been changed without your permission, change it back to what it used to be or to whatever you like it to be now.
Now go to the History menu and select the Clear History option.
Do the same to all other browsers you may have in your computer – here are examples with Chrome and Firefox.
Cleaning Chrome
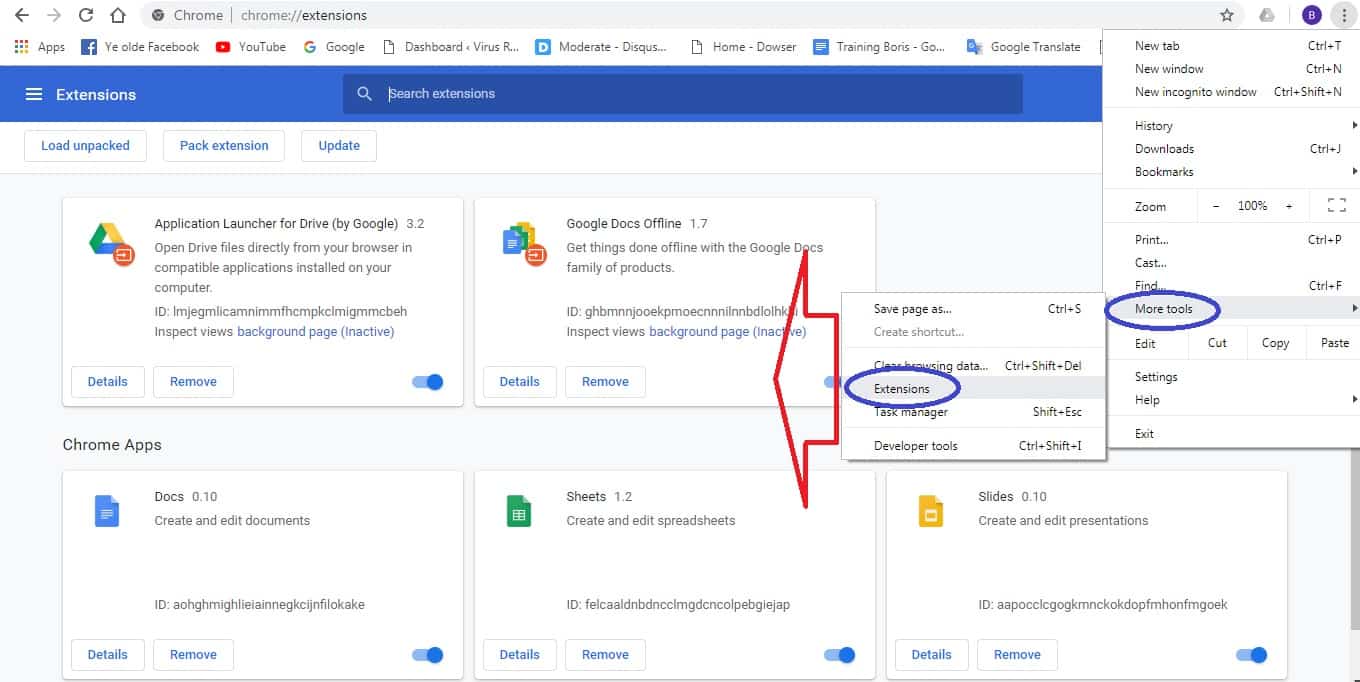
Open Chrome and open its main menu, then go to More Tools > Extensions. Click on the Remove button next to all of the extensions that you do not trust.
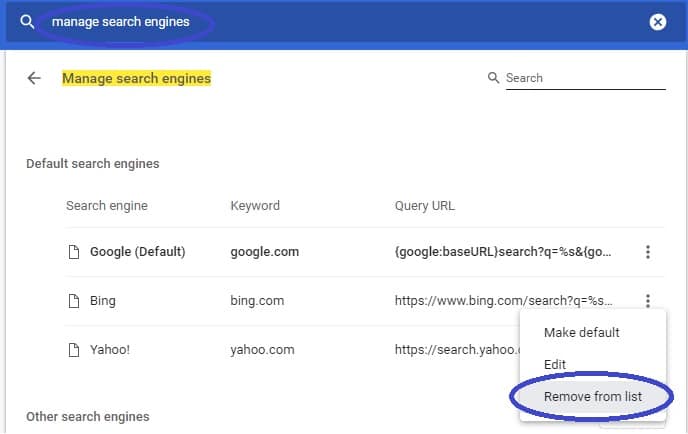
Next, from the main menu, go to Settings and type Manage Search Engines in the search bar. Open the result that shows up and then delete all search engines other than the one you normally use by clicking on the three-dot icon next to the other ones and selecting Remove from list.
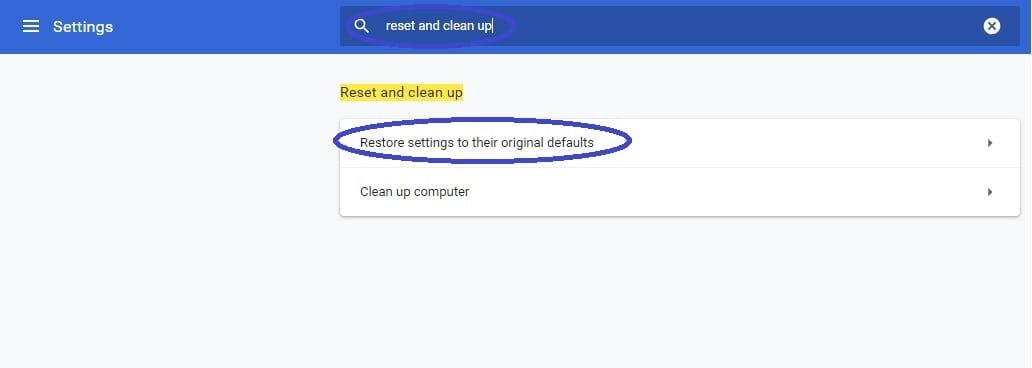
Back in Settings, type Reset and clean up and open the option that shows up (Restore settings to their original defaults). Confirm by selecting Reset Settings.
Cleaning Firefox
Open Firefox and then open its main menu. Go to Add-ons and open the Extensions menu from the left. Look at the extensions and Remove the ones you do not trust.
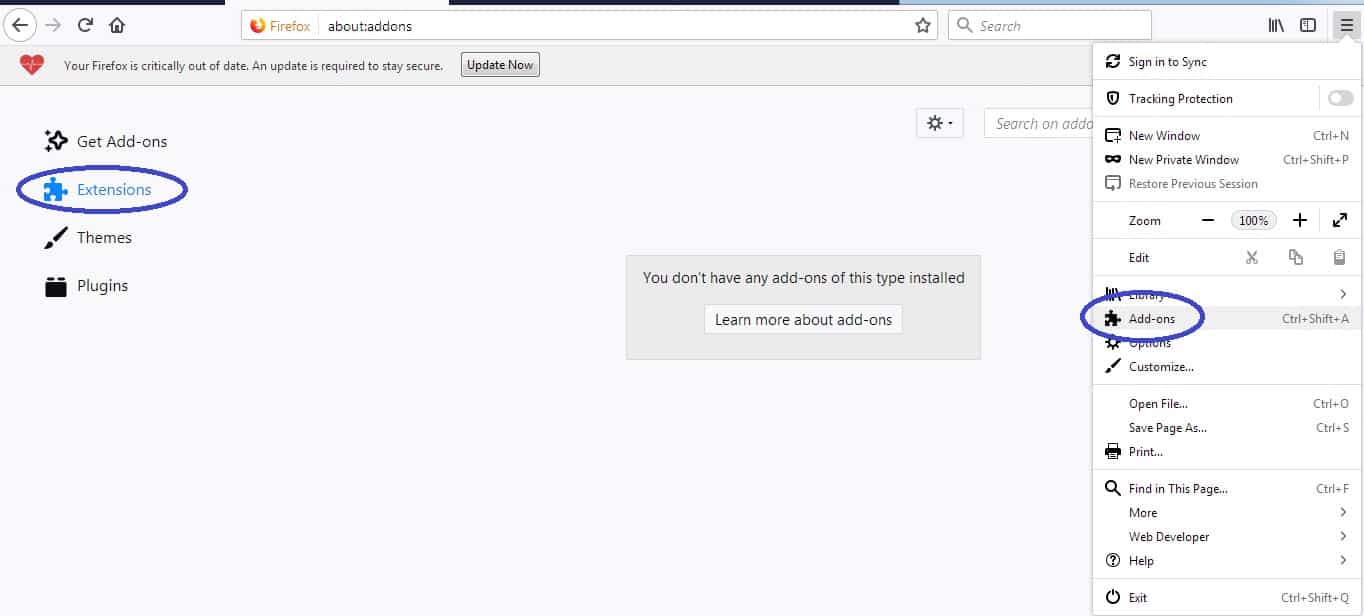
Next, open the menu again, go to Help > Troubleshooting information and in the page that opens, select Refresh Firefox and then confirm the action in the window that opens.