CrescentCore in Depth
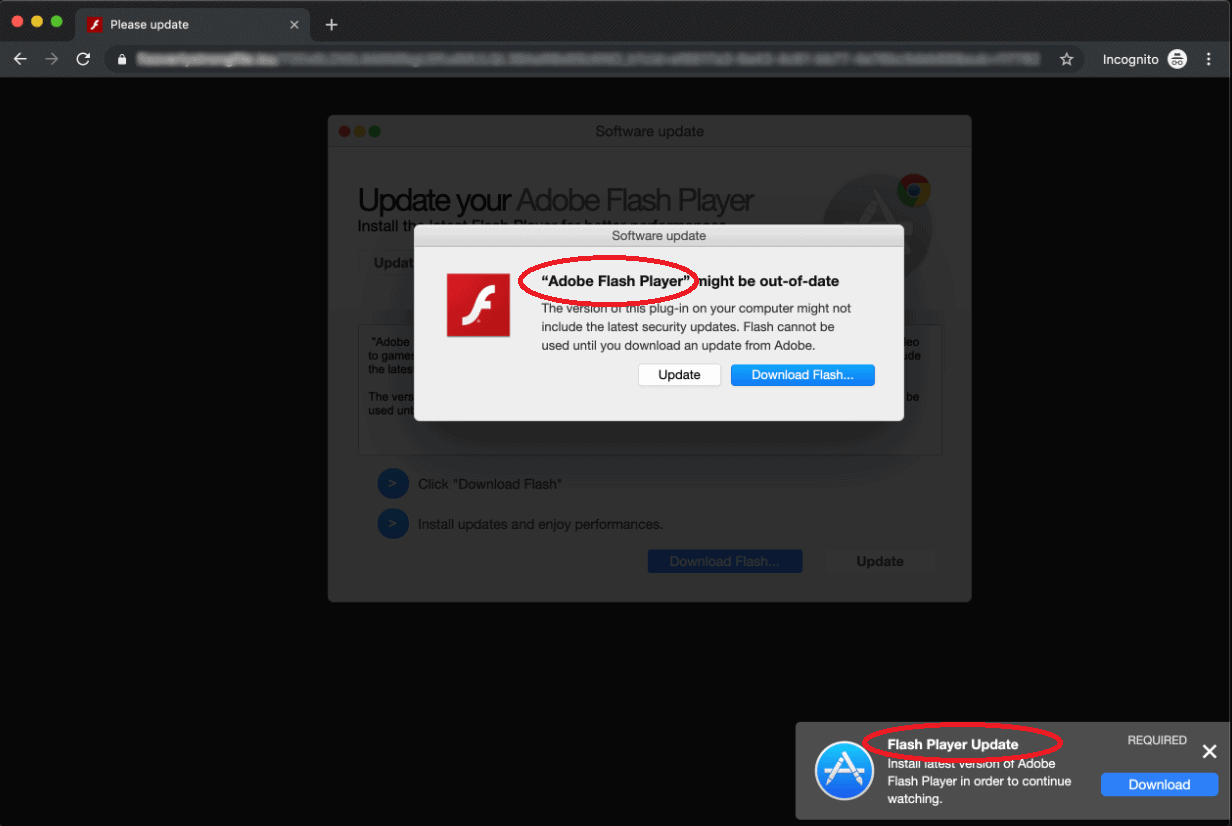
I am sure that most of you are familiar with the computing term “Trojan Horse” – most computer users have, at the very least, heard about the infamous Trojan Horse malware threats and know to keep away from them. However, simply knowing that a Trojan Horse is something that’s bad for your computer isn’t enough. One must also know how to protect their machine against such threats, what those infections can do if they enter the system and what the best ways of removing a Trojan is in case such a virus manages to infiltrate the computer. Here, you will learn some basic information about all those things. The thing that inspired the writing of this article is a malicious program named CrescentCore. CrescentCore Malware, as you have probably already guessed, is a Trojan Horse representative. Recently, many users have gotten their machines invaded by the CrescentCore infection and if you are among them, you will probably benefit from reading this post and from checking out the removal guide attached to it. However, even if you have accidentally landed on this page while looking for something else, it would still be a good idea to inform yourself about the characteristics of this newly released malware threat.
If you have landed CrescentCore, “Flash Player Auto Update Daemon” or LoudMiner without really being sure how it has happened, know that there are quite a few ways a Trojan can infiltrate a given computer. Oftentimes, infections like this are added inside files that you can download from the Internet. The carrier files tend to look harmless on the outside so that the user would get tricked into executing them. Oftentimes, those files would be the installers of some popular video games that have been pirated and are now getting distributed illegally. However, you can also land a Trojan if you click on some online ad message or clickbait download button that get presented to you inside some obscure and questionable sites. For instance, gambling sites and sites with adult content oftentimes tend to show unreliable and sketchy ads within their pages that may redirect you to online addresses filled with malware and Trojans. Spam is yet another very popular distribution method used to get Trojan Horses inside more and more computers. Therefore, opening any link or file included in an online message or e-mail that looks like spam is highly inadvisable.
Is CrescentCore Malware Dangerous?
But what happens after the infection? Well, there are actually quite a few things that may happen – your online usernames and passwords may get stolen, you may lose control over your computer, some data on you machine may get encrypted if the Trojan has backdoored a Ransomware cryptovirus inside your machine, as well as many many more. The Trojans like CrescentCore are known for their versatility and this is why this type of infections is so popular and widespread. The key thing is to manage to remove them as soon a possible or else the consequences of their attacks may be quite nasty. Here, you can learn more about how you can remove the CrescentCore Trojan from your machine.
SUMMARY:
| Name | CrescentCore |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | A Trojan may make your computer behave in an unusual way by triggering errors and BSOD crashes but there may also be no visible symptoms at all. |
| Distribution Method | Sites that spread pirated content as well as adult and gambling sites are oftentimes sources of Trojans. |
[add_third_banner]
Remove CrescentCore Malware
Step 1: Closing Safari (or any other browser that you may be using at the moment)
First, you will need to close your browser if it is still open. If you can’t do that normally, you will need to Force Quit it:
Open the Apple Menu and select Force Quit to do that. You can also use the ⌘ key + Option Key combination to open the Force Quit Applications dialog box. In this box, select the Safari browser (or whatever browser you are using) and then click on the Quit button. Confirm the action by selecting Force Quit again.
Step 2: Killing suspicious processes
Open Finder and go to Applications > Utilities and then open Activity Monitor. Now take a careful look at the processes there – look for any that seem suspicious, unknown and questionable. If you think that a given process may be the culprit behind the issue or may at least be related to it, highlight it with the mouse and select the i option at its top.
In the box that opens, click on Sample.
Scan the sample files with the online scanner we have on this page and if any of them get flagged as malicious, delete them and then kill their processes.
Step 3: Safely launching the browser
Hold the Shift from your keyboard and then launch Safari – holding Shift will prevent any previously opened pages to load again, just in case any of them were related to the problem.
If any problematic pages still load after you safe-launch the browser, then do the following:
Force-Quit the browser (Safari) again and then turn off your Wi-Fi connection by clicking on the Wi-Fi off option from the Mac Menu. If you are using cable Internet, simply disconnect the cable from your Mac.
Step 4: Uninstalling suspicious extensions
After you safe-launch Safari and are sure none of the previously opened pages load now, go to Preferences > Extensions.
Select and uninstall (by clicking on the Uninstall button) all extensions there that are unfamiliar to you or that you think may be suspicious. If you are not sure about a certain extension, it’s better to uninstall it – no extension is required for the normal functioning of the browser.
Step 5: Cleaning Safari
If you have other browsers aside from Safari, do the following:
In Safari, open Preferences from the browser’s menu and go to Privacy.
Select Remove All Website Data and then Remove Now. Note that this will delete all stored site data including any saved passwords and usernames. In other words, you will have to manually log-in to every site where you have a registration so make sure you remember your usernames and passwords.
Back in Preferences, click on General and see what your Safari’s homepage is. If it has been changed without your permission, change it back to what it used to be or to whatever you like it to be now.
Now go to the History menu and select the Clear History option.
Do the same to all other browsers you may have in your computer – here are examples with Chrome and Firefox.
[add_forth_banner]
Cleaning Chrome
Open Chrome and open its main menu, then go to More Tools > Extensions. Click on the Remove button next to all of the extensions that you do not trust.

Next, from the main menu, go to Settings and type Manage Search Engines in the search bar. Open the result that shows up and then delete all search engines other than the one you normally use by clicking on the three-dot icon next to the other ones and selecting Remove from list.

Back in Settings, type Reset and clean up and open the option that shows up (Restore settings to their original defaults). Confirm by selecting Reset Settings.

Cleaning Firefox
Open Firefox and then open its main menu. Go to Add-ons and open the Extensions menu from the left. Look at the extensions and Remove the ones you do not trust.

Next, open the menu again, go to Help > Troubleshooting information and in the page that opens, select Refresh Firefox and then confirm the action in the window that opens.

Leave a Reply