Remove 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM Bitcoin Email Virus
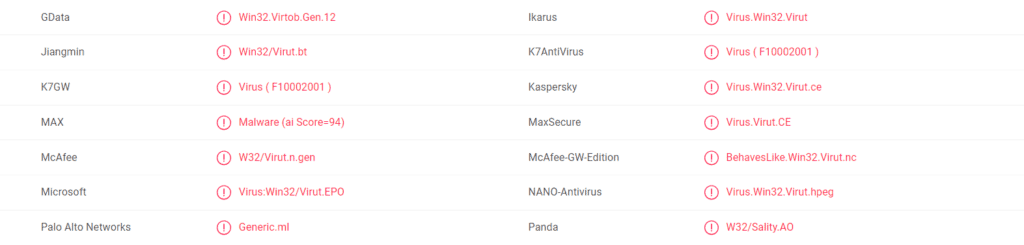
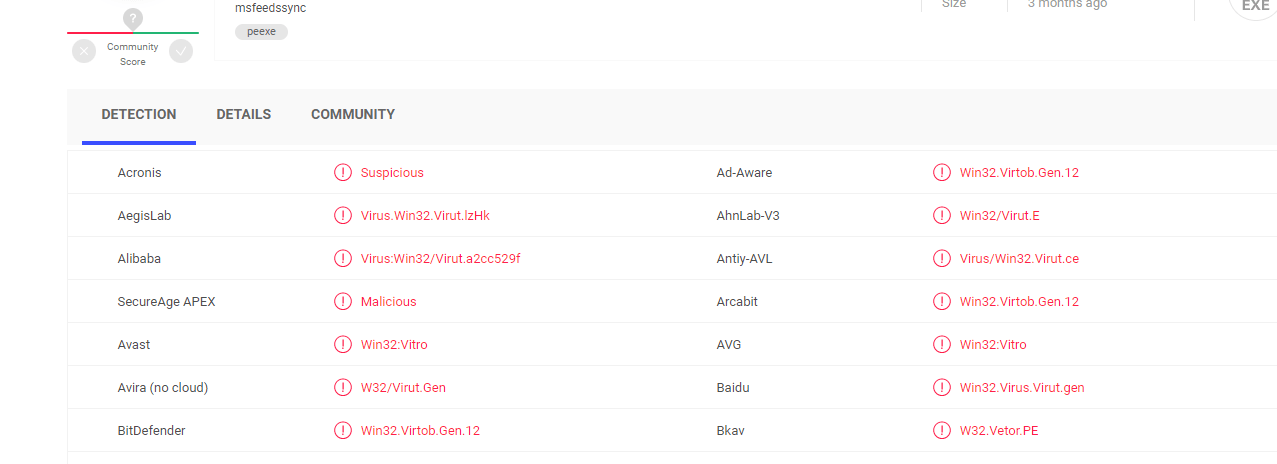
15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM – Details
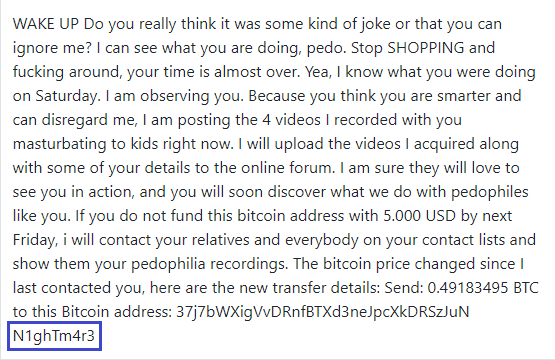
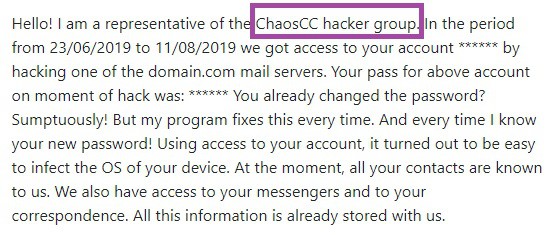
Our users reported that they have received a scam email with 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM Bitcoin Wallet with the following text:
Hello! I have very bad news for you. Blah blah. I just hacked this router and placed my malicious code on it. When you went online, my trojan was installed on the OS of your device. After that, blah A month ago, I wanted to lock your device and ask for a not big amount of btc to unlock. But I looked at the sites that you regularly visit, and I was shocked by what I saw!!! I’m talk you about sites for adults. I want to say – you are a BIG pervert. Your fantasy is shifted far away from the normal course! And I got an idea…. Joys blah I’m know that you would not like to show these screenshots to your friends, relatives or colleagues. I think $981 is a very, very small amount for my silence. Besides, I have been spying on you for so long, having spent a lot of time! Pay ONLY in Bitcoins! My BTC wallet: 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM
The thought that your computer might have been secretly compromised by a Trojan Horse is a scary one. But what could be even scarier is to receive an email from a hacker claiming that he has gained full access to your machine without your knowledge with the help of a hidden Trojan horse infection. The later, in fact, has recently become a base for a viral email BitCoin scam which is rapidly taking over the internet. The victims of this new email scam have been reporting that they have been receiving ransom-demanding emails from a hacker, who is asking them to pay a certain amount of money to a given BitCoin wallet. The crook threatens that if no money enters his account, he will do something bad to the machine which he has already compromised with hidden malware. The supposedly “infected” system will be damaged in a serious way or some sensitive personal information, such as passwords, embarrassing images, personal files, documents, etc. will be made public. Professionals in the security sector are warning, however, that the claims in such phishing emails should not be trusted or taken for real without any actual proof of malware infection because, in most of the cases, they are sent by people with malicious intentions whose idea is to simply trick the web users into sending their money. The problem is, there are many email scams with similar scenarios nowadays and while some of them may be a bluff, others may really turn out to be carriers of nasty infections such as Trojans, Spyware, Rootkits and similar viruses.
Removing 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM manually
For instance, the name of a fairly new Trojan-based threat known as 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM Bitcoin Email could be linked to email BitCoin scam messages like the ones that we describe because carriers of this infection could be various phishing messages, spam and scam emails. That’s why in case you have recently been spammed with an email of this type, it is highly recommended to scan your computer with a reliable security tool and remove any threat that it detects. The reason is, threats like 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM , “You got infected with my malware”, “Save Youself” can sneak inside the system unnoticed and without showing any visible symptoms but once they nest inside, they really can provide their criminal creators with remote access to the infected machine, steal passwords, sensitive information and other details related to the victim. That’s why you should not simply delete the blackmail spam email from your inbox but carefully check the entire PC for potentially hidden malware that could be operating silently in the background. Sometimes, the Trojans may transmit different information to remote servers without any visible indication or to create room for other viruses and infections such as Ransomware or Spyware. The good news is that, in the removal guide below, you will find instructions on how to scan your computer entirely and remove 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM and any related components that might be hiding inside your system. For best results, you can use the attached professional scanner for quick detection in a combination with the detailed steps for manual deletion.
SUMMARY:
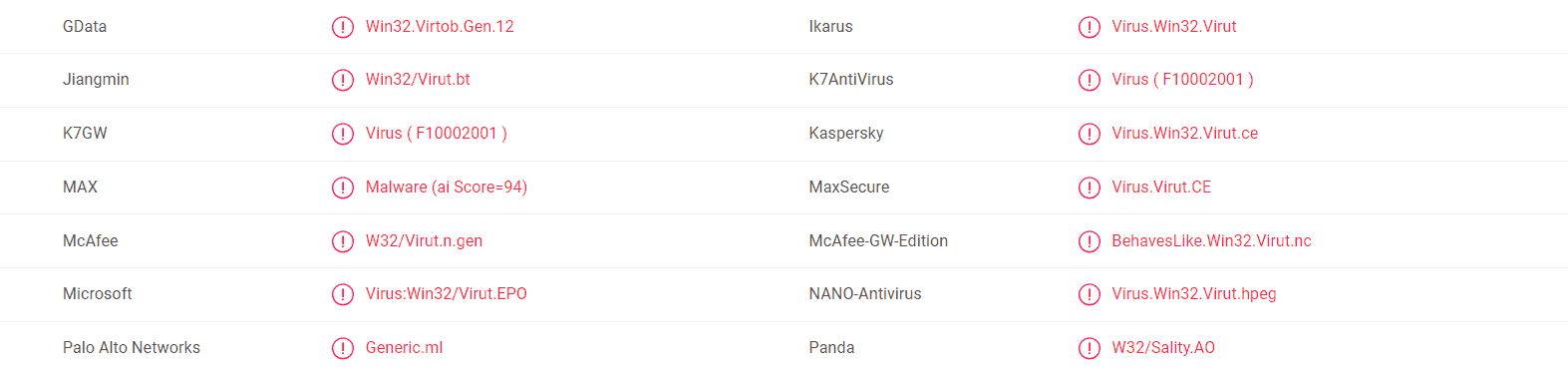
| Name | 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | Trojans rarely show visible symptoms of their presence but sometimes email scams may reveal a possible infection. |
| Distribution Method | Software installers with compromised content, torrents, spam messages, malicious emails and attachments, fake ads. |
Remove 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM Bitcoin Email Virus
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
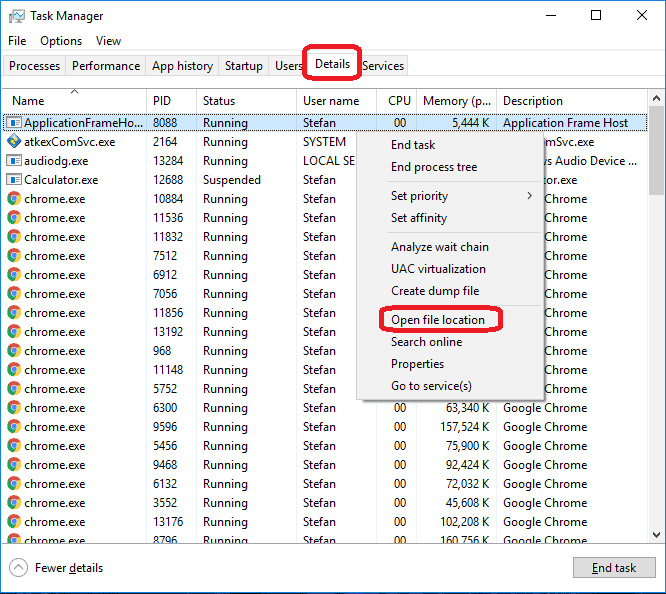
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM .
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:
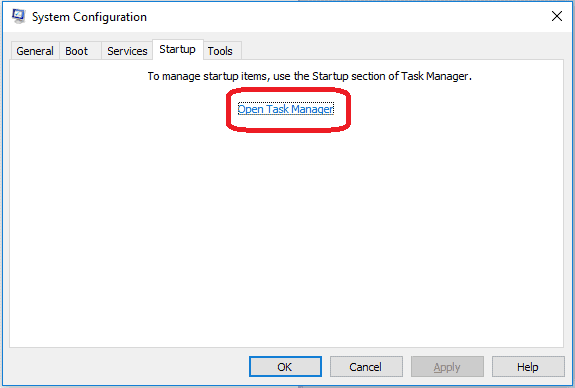
If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to 15yF8WkUg8PRjJehYW4tGdqcyzc4z7dScM . About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.