14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y – Details
A number of web users have recently fallen victims to a shady email BitCoin 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y scam . The scenario of that scam is very simple, yet very effective in terms of getting the victims panicked and getting them to pay a ransom to the hackers behind the scheme. It involves sending a threatening phishing email message, like 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y, which informs the users that their computer has been compromised by a hidden malware and that they have to send a certain amount of money to a given BitCoin wallet if they want to save their system and regain their virtual privacy. The crooks behind the 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y scam typically claim that they have gained remote access to the computer and have gotten their hands on some personal data such as passwords and sensitive photos. They usually threaten to make this data publicly available or maybe damage the computer if no payment is released. Unfortunately, the number of users who have already been greeted by phishing emails like 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y has been rapidly growing in the recent days and some of them have already been tricked into paying the ransom. The security experts, however, inform that in most of the cases the things written in these messages like 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y, are nothing more than bluffs which aim at extorting money from the scared victims. Trusting the claims that are stated there is not advisable but it is worth to mention that, sometimes, the BitCoin scam emails could be related to the distribution of real Trojan Horse infections. That’s why they should not be just ignored.
Can I remove 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y myself?
For instance, one recently reported Trojan-based infection named 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y could be linked to such emails and, if you have recently happened to interact with a message of this kind, it is a good idea to check your system for any possible contaminations. The fastest way to do that is by using a professional software protection tool such as the one that you can find below or by running a full system check with your current antivirus program (in case you have one).
If the scan shows that your computer is clean, then you most probably have been spammed with a fake message, the only aim of which is to trick you into sending your money to some dishonest people. If you detect 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y or some other Trojan, however, then you may be in real trouble because such Trojan-based infections can hide in the system for an indefinite period of time and wait for the commands of their creators. Such an infection can weaken your computer’s safety by creating security holes and inviting other malware such as Ransomware or Spyware in the system without your knowledge. If not removed on time, 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y may not only trick you into sending money to anonymous hackers but may also severely damage your machine, delete important data, exploit the system’s resources and provide the hackers with full remote control. That’s why it is very important to carefully check your entire computer and remove anything that might be related to the infection in order to prevent it from doing something really bad.
I made a video showing how you satisfy yourself in the left half of the screen, and in the right half you see the video that you watched. With one click of the mouse, I can send this video to all your emails and contacts on social networks. I can also post access to all your e-mail correspondence and messengers that you use. If you want to prevent this, transfer the amount of $775 to my bitcoin address (if you do not know how to do this, write to Google: “Buy Bitcoin”). My bitcoin address (BTC Wallet) is: 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y
14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y SUMMARY:
| Name | 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y |
| Type | Trojan |
| Danger Level | High (Trojans are often used as backdoor for Ransomware) |
| Symptoms | Scam messages in your email inbox may eventually indicate the presence of a Trojan inside the computer. |
| Distribution Method | Various transmitters, such as malicious ads, infected links, spam email messages, harmful attachments, cracked software, torrents, and more. |
[add_third_banner]
Remove 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y Bitcoin Email Virus
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
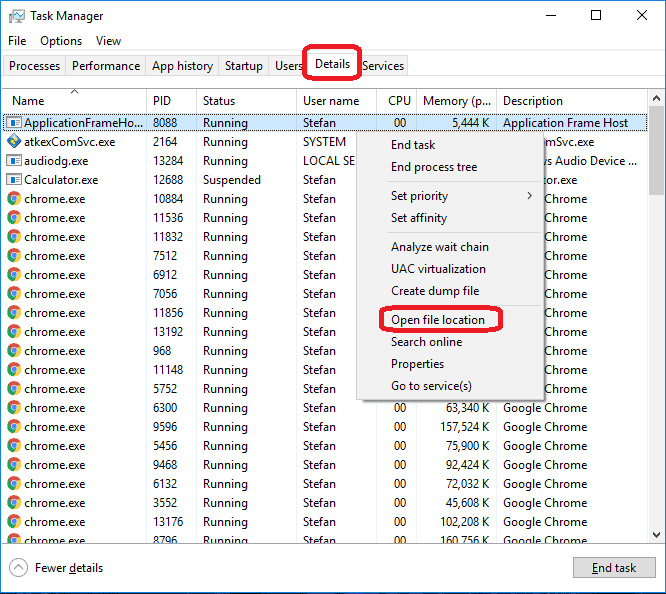
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to 14tfS3yWL2cABhXVJZ97XRhuDXC69aWH6Y Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
Leave a Reply