About the Mtogas Virus
Any infection that belongs to the Ransomware family must be seen as a serious threat to your computer’s security and must be kept as far away from your system as possible. However, as you cannot know the exact sources of each and every piece of malware from this category or from another one, it is perfectly possible that you get your system infected even if you have been cautious and vigilant while online. And, if the malware program that has infected your computer is a Ransomware cryptovirus like Mtogas, then you really don’t have a lot of options. Here, however, we will do our best to give you useful advice on how to act in such a situation and we will tell you about the options you may have so that you can decide what to do next. The file-encrypting viruses like Mtogas, Krusop, Masok are definitely not something you’d like to land on your computer but with the right guidelines and with some luck, you may just be able to minimize the harm that such an infection may have caused.
Alternatives for encrypted .mtogas files

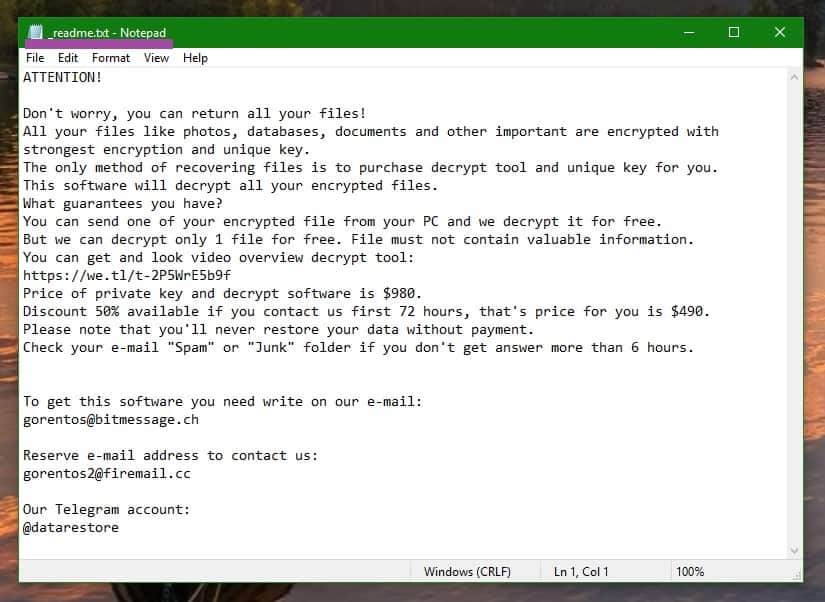
As you are probably aware, the purpose of a cryptovirus Ransomware infection is to extort money from its victims. The way such a virus is able to do that is through the use of the otherwise harmless process of file-encryption. Once the malware piece enters the computer, it “takes hostage” the personal files of the user by locking them with its advanced encryption. The files stay intact but can no longer be accessed through any regular means that the malware victim may have at their disposal. After the encryption, the only surefire way of opening any of the files is through the use of the unique key that corresponds to this particular encryption algorithm. It is exactly this key that the hackers behind Mtogas are readily offering you in exchange for a ransom payment. Depending on the specific Ransomware and who or what the victim is, the requested sum may vary greatly. In most cases, however, it will, at the very least, be a couple of hundred dollars. It is understandable if paying such a sum to get your files back isn’t perfect for you. Also, it’s important to mention that paying doesn’t actually mean that you will definitely get your files restored. For all you know, the hackers may simply be lying to you in order to get your money – they may not really have a working key or they may decide that they simply won’t send you anything after the money is received. The point is, you can never be really sure what to expect and that is why paying the ransom isn’t perfect. Ideally, if you have a backup of your files, all you’d need to do is use our removal guide for Mtogas to eliminate the Ransomware and then restore the files from the backup. If you don’t have a backup, you can use our second section of he guide where you can find some alternative file-recovery suggestions. Keep in mind, though, that those may not always work and we can’t give you any guarantees about the future of your data.
SUMMARY:
| Name | Mtogas |
| Type | Ransomware |
| Danger Level | High (Ransomware is by far the worst threat you can encounter) |
| Symptoms | Ransomware threats typically operate in secrecy and stealth and only reveal themselves when its time for the blackmailing harassment to begin. |
| Distribution Method | A virus like this may get delivered to your computer through the help of a Trojan backdoor. |
[add_third_banner]
Remove Mtogas Virus
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to Mtogas
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the Mtogas.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and Mtogas , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – Mtogas
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to Mtogas Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
7: Mtogas Decryption
The previous steps were all aimed at removing the Mtogas Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them. For that, we have a separate article with detailed instructions on what you have to do in order to unlock your data. Here is a link to that guide.
Leave a Reply