This page aims to help you remove .Leto for free. Our instructions also cover how any .leto file can be recovered.
.Leto
.Leto is a new cryptovirus of the Ransomware type. Having .Leto on your computer will result in getting your files encrypted.
If this infection is what brought you here, we will do our best to help you remove it. The removal guide that you will find below is planned specifically for this purpose, and will show you all the necessary steps that you must complete. Deleting the virus alone, however, may not restore the access to your files. That’s why we’ve also included steps to help you retrieve your encrypted data, but we can’t promise they’ll work for all the files. Please, read on, and we’ll clarify the details of the malware you’re currently facing, as this is crucial for dealing with it and preventing anything like this from happening again.
The .Leto virus
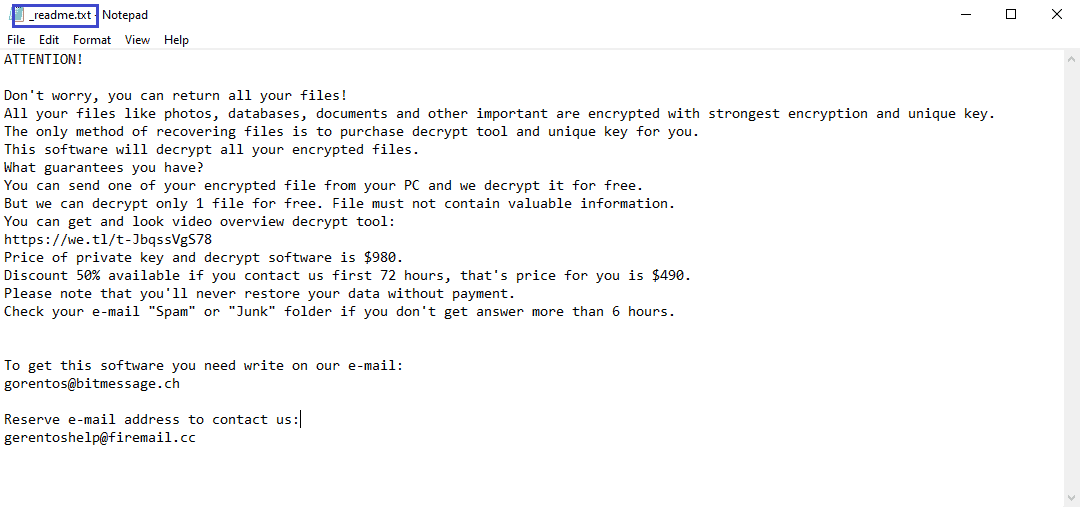
The .Leto virus is a file-encrypting program that is used extort people’s money. The .Leto, .Reco and .Bora viruses are part of the DJVU Family and their goal is to force you to pay money for the release of your data.
Security experts have been warning that there have been cases where victims of ransomware have paid the ransom for their files, but have never got the decryption key needed to unlock them. Therefore, if you have been considering the ransom payment as an option to get your encrypted data back, we suggest you read on. Paying the criminals behind the ransomware is only a form of sponsorship to their blackmailing practice. At the same time, the decryption key they promise to send you once you pay may not even exist. Or, if there is indeed such a key, it may simply fail to decrypt all the files, and end up being a costly waste of money.
The .Leto file encryption
The .Leto file encryption the process that is responsible for the lockdown on your files. During the .Leto file encryption, there are hardly any symptoms.
When the malware invades a targeted computer, it immediately scans it for the most commonly used files, and automatically encrypts those files. In some cases, the file extensions may get changed to some extension that cannot be opened or recognized by any program. After the encryption has been completed, the ransomware announces its presence and the damage it has done, through a ransom note. This note usually contains information about the ransom amount, how to pay it, and probably a deadline as well. Different threatening tactics are commonly used by the hackers in order to throw their victims into panic and to give them as little time as possible to look for alternative solutions.
We, however, advise you to do just that – take your time, and carefully research for available alternatives that may help you remove .Leto, and recover your files. Ideally, you can use your own backups to recover the encrypted information, or extract some files from the system itself. Or, you can check our daily-updated list of free decryptors, and see if there is a reliable solution to the encryption that has been applied to your data. Don’t forget to scan your computer with a reliable security tool, tough. This will help you remove all the malware, and protect your system in the future.
SUMMARY:
| Name | .Leto |
| Type | Ransomware |
| Danger Level | High (Ransomware is by far the worst threat you can encounter) |
| Symptoms | Very few and unnoticeable ones before the ransom notification comes up. |
| Distribution Method | From fake ads and fake system requests to spam emails and contagious web pages. |
[add_third_banner]
Remove .Leto Ransomware
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to .Leto
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the .Leto.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and .Leto , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – .Leto
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to .Leto Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
7: .Leto Decryption
The previous steps were all aimed at removing the .Leto Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them. For that, we have a separate article with detailed instructions on what you have to do in order to unlock your data. Here is a link to that guide.
Leave a Reply