About the .Nasoh virus
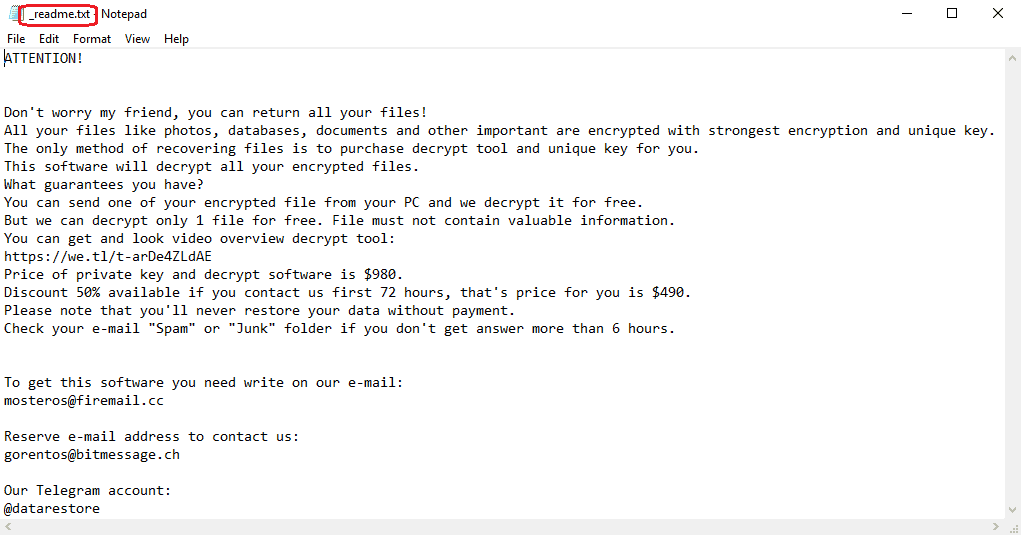
If you get attacked by a Ransomware cryptovirus this could deprive you of accessing your most important files. Your documents, archives, databases, images, videos, audios and other commonly used files may suddenly become encrypted with a secret algorithm, which renders them inaccessible. No matter what you try to do, you will not be able to open or use any of your files without paying a certain amount of money to the hackers who are keeping the corresponding decryption key. This is exactly what can happen if your system has been compromised by one of the latest Ransomware infections called Nasoh. This threat is designed to blackmail random web users, businesses and even big governmental institutions and to extort money from them in order to restore the encrypted files to their previous state.
The attackers, who stay behind the infection, typically generate a ransom-demanding notification on the screen of the infected machine immediately after the secret encryption process has completed. The victims usually get scared and quite shocked to detect such a message on their monitor and don’t know what to do. If you have recently been greeted by a notification that asks you to pay a certain amount of money to a given cryptocurrency wallet, you may well be feeling frustrated and you may be searching for a highly effective course of action that can help you avoid the ransom payment. Fortunately, on this page, we are happy to provide you with some alternative methods which may help you to remove Nasoh and potentially recover your encrypted files.
Compared to other malware types, computer infections like Nasoh, Coharos or Mtogas have a great advantage – they are extremely stealthy and may oftentimes remain under the radar of most antivirus programs. This is because, instead of causing some real system damage, which can be detected by the security software, the Ransomware threats use file-encryption as a foundation to their blackmail scheme, which is actually not a harmful process. File encryption is a common process for the system since we need it to keep sensitive information safe and protected from unauthorized access. We use encryption on a day-to-day basis when searching the Internet, when paying online, when using our e-banking, when chatting, etc. For this reason, most of the antivirus programs on the market do not consider the encryption as something unusual or malicious, and they normally do nothing to stop it. This helps the Ransomware to apply its encryption without any disturbance and then surprise us with a threatening ransom-demanding notification when it is finished.
The .Nasoh file-encryption goal

The goal of Nasoh and its terrible blackmail scheme is to extort money from as many people as possible. The crooks behind the scheme may use different threatening scenarios in order to make the victims pay as fast as possible. They may even promise to send a special decryption key immediately after the payment is made. Some crooks may go as far as giving you to test-decrypt a file or two, just to make you believe them. If you pay, however, you will basically be sponsoring the criminals to create more Ransomware and infect more users with it. Not to mention that there is nothing that could make them fulfill their promise and you may never receive any decryption solution in return for your money.
For this reason, we typically advise the people who land on our “How to remove” guide to seek alternative options of dealing with the Ransomware, before choosing the ransom transaction. One such option is the Removal Guide below.
SUMMARY:
| Name | Nasoh |
| Type | Ransomware |
| Danger Level | High (Ransomware is by far the worst threat you can encounter) |
| Symptoms | Very few and unnoticeable ones before the ransom notification comes up. |
| Distribution Method | From fake ads and fake system requests to spam emails and contagious web pages. |
[add_third_banner]
Remove .Nasoh Ransomware
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to Nasoh
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the Nasoh.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and Nasoh , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – Nasoh
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to Nasoh Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
7: Nasoh Decryption
The previous steps were all aimed at removing the Nasoh Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them. For that, we have a separate article with detailed instructions on what you have to do in order to unlock your data. Here is a link to that guide.
Leave a Reply