It is not a secret that the Internet is full of nasty computer threats that only wait for you to click on their carriers so that you get your PC infected with them. Ransomware, Spyware and all sorts of malicious programs could sneak inside your PC in no time should you lose your caution for a second and interact with the wrong piece of online content. On this page, however, we will focus on one particularly nasty threat named “I hacked your device” which originates from the Trojan Horse family. As a newly reported Trojan-based infection, “I hacked your device” is quite sophisticated and has the ability to sneak inside a targeted machine any given device if the user isn’t careful without triggering any visible symptoms of its presence. This makes it extremely dangerous and helps it to quickly spread across the web on various devices. If you have had the misfortune of getting infected with this piece of malware, we are determined to help you remove the nasty Trojan as soon as possible and prevent the possible harm that it may cause. That’s why, in the next lines, we have prepared a set of manual instructions and a helpful automatic “I hacked your device” removal tool for a full system scan. Mail scams are one of the most widespread methods that online crooks use to extort money. Most common examples of such a scam is when a “hacker” sends you an online letter in which he claims that he has managed to infect your computer with a Trojan Horse virus and now has full access to your system and files.
One similar letter is this one:
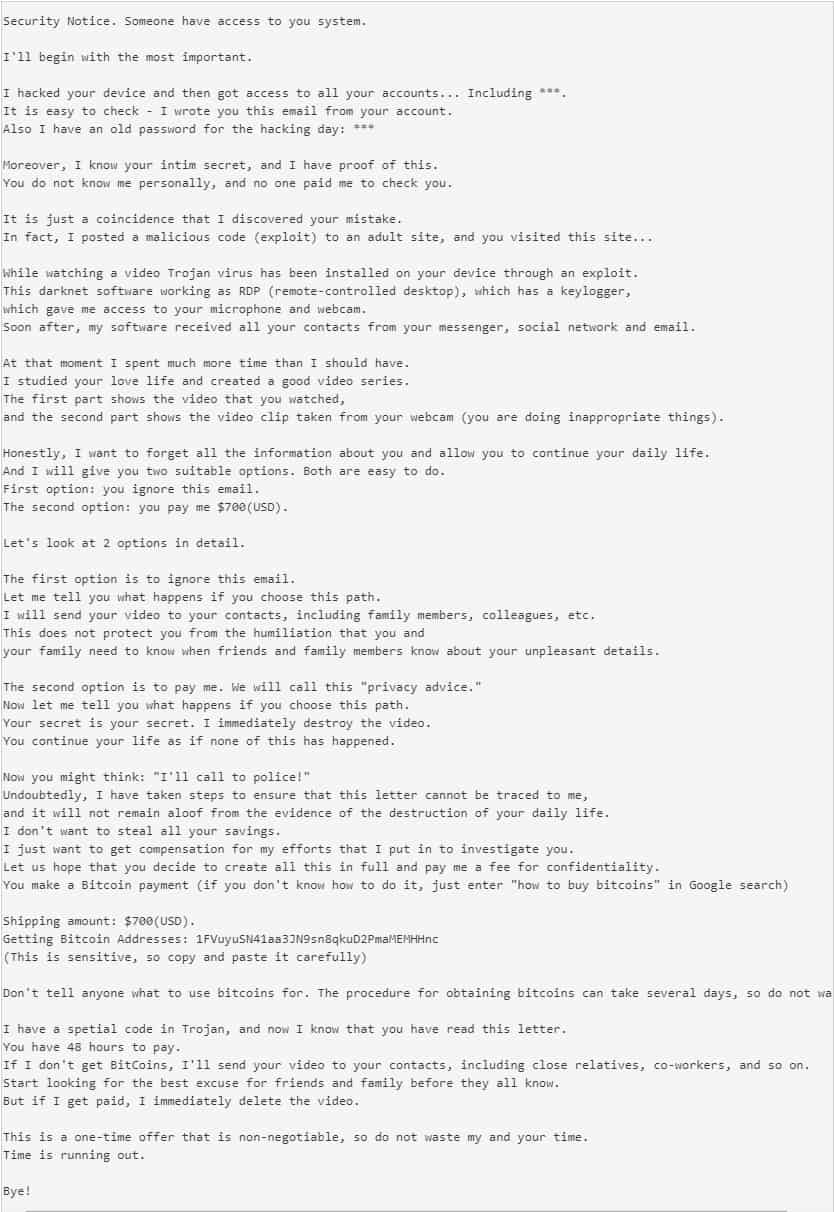
What damage may “I hacked your device” cause if not removed on time?
The reason we urge you to follow the instructions below and remove “I hacked your device” as soon as possible is that, if it remains in the system any longer, you cannot predict the scale of the damage that it may cause. An advanced malicious program from the Trojan Horse type could corrupt your system in a very serious way, sometimes, to such an extent, that you may not be able to repair it without reinstalling the whole OS. Unfortunately, you cannot be sure what exactly the malware might be programmed to perform. That’s why the best you could do in case you detect “I hacked your device” on your machine is to immediately take action and search for the fastest and the safest methods (like the ones on this page) that can allow you to remove it.
If you don’t manage to remove the malware on time, the crooks may use “I hacked your device” for a whole list of possible criminal actions ranging from deletion of personal data, modification of system files and processes, espionage, theft of passwords and login credentials, theft of financial details and even insertion of other viruses. In many of the cases, the Trojan can provide its creators with unauthorized remote access to the entire computer. And, as you may have guessed, the crooks aren’t going to use it for any good. They can badly mess up everything that you keep in the system and even insert threats like Ransomware or Rootkits in your PC without your knowledge. Sadly, unlike other viruses which typically trigger some symptoms of their presence, Trojans like “I hacked your device” usually lack any visible indications which can give them away. That’s why it is really important that you have a reliable antivirus program which can scan the system for hidden threats and allow you to eliminate them before any major harm has been caused by them. In case that you don’t have such a program, we really advise you to get one because, even if you do your best to keep away from potential malware sources (such as shady links, fake ads, spam emails, pirated content and phishing pages), there is always a chance that you may get tricked into clicking on something harmful and still get infected without knowing it.
SUMMARY:
| Name | “I hacked your device” |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | In most of the cases, the Trojan doesn’t show any specific symptoms of its presence. |
| Distribution Method | Spam emails, malicious attachments, infected installers, Malvertising, pirated content, adult sites. |
[add_third_banner]
Remove “I hacked your device” Email Virus Scam
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: The Hosts file
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the virus.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to “I hacked your device”. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
Leave a Reply