About David Ghost Email Blackmail Scam
Some of our users reported a David Ghost Email Blackmail scam that they have received, with the following message:
Hey!
I know your pass is: *********
I infected you with my private malware, (RAT) / (Remote Administration Tool), a few months back when you visited some website where my iframe was placed and since then, I have been observing your actions.
The malware gave me full access and control over your system, meaning, I can see everything on your screen, turn on your camera or microphone and you won’t even notice about it.
I have also access to all your contacts, private pictures, videos, everything!
I MADE A VIDEO showing you (through your webcam) STATISFYING YOURSELF!
You got a very good taste! Hahaha…
I can send this video to all your contacts (email, social network) and publish all your private data everywhere!
Only you can prevent me from doing this!
To stop me, transfer exactly 1200$ with the current bitcoin (BTC) price to my bitcoin address.
I think it’s a very good price compared to the damage and hell it can bring into your life!
If you don’t know how to get bitcoin, Google – “How to buy Bitcoin”.
The wallet you can create here: www.login.blockchain.com/en/#/signup/
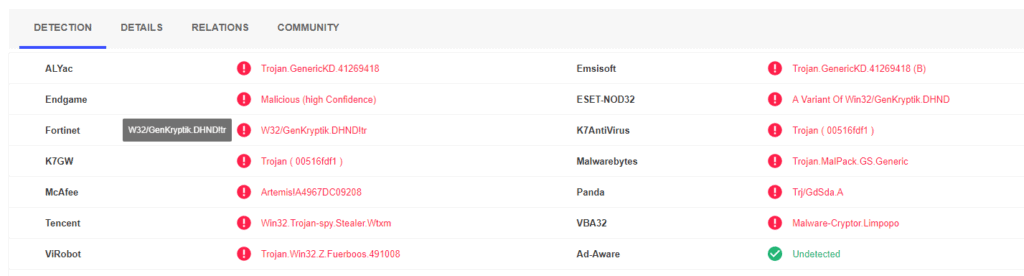
A majority of antivirus programs have detected the virus using David Ghost Email Blackmail. You can see the attached report from VirusTotal below:
David Ghost
Typically, the Trojan-based infections may perform many different activities, which may be aimed at stealing your personal information, hacking into your accounts, spying on you, messing with your data and even blackmailing you through various criminal schemes. They are often being spread via fake emails, spam messages, intriguing offers, attachments and other types of web content. That’s why, in case that you have recently come across some phishing email messages or blackmailing or if you have clicked and opened something suspicious, it is a good idea to check your system for hidden threats of this type.
The Trojan Horses (1HB3KtKoguFuZ4BdmCv9Fc4tYTwDQgmqmW, Cve-2019-1663) are well known software threats and most users have some form of security program on their machines that can fend off the majority of malware infections, there’s always a risk of landing something dangerous and if that something is a Trojan, then actions towards removing the infection should be taken immediately or else the consequences of the attack can be very severe.
Here, in this particular post, you can learn some important and helpful information about a virus program called David Ghost Email Blackmail. This is a newly released representative of the Trojan Horse family and it s currently out there, on the Internet, seeking its latest victims. Sadly, the information we have about it is isn’t detailed enough and more research needs to be done, which is why it is still unclear what it’s specific task would be in each instance it infects a given machine. You see, a major difference between an infection like David Ghost Email Blackmail and a malware program from some other category (Ransomware, Spyware, Rootkits, etc.) is that the Trojans like David Ghost Email Blackmail may have many different uses and may even get reprogrammed to do something different from what its initial purpose might have been. In contrast to that, most other types of malware infections would have one or two very specific uses and they wouldn’t do anything beyond their initial purpose.
Though we do not know the exact goal of this Trojan, we can give you an idea about what you may expect from such an infection. The Trojan viruses are oftentimes used as tools of data corruption and system destruction but that is certainly not the only thing they could be employed for. Other potential uses of a Trojan include theft of personal info through various espionage techniques, remote control over the infected machine, backdoor activities for other malware infections (especially Ransomware), etc. A Trojan oftentimes has a whole network of infected computers – such networks are called botnets and are used for activities such as DDoS attacks, spam e-mail distribution and cryptocurrency mining. All in all, the viruses of this type are like the Swiss-Army knife of the computer malware – they can be used in various ways and their goals may get altered on the go. This is why the Trojan infections, especially newer ones like David Ghost Email Blackmail, tend to be very unpredictable.
Stopping a Trojan David Ghost Email Blackmail
Another problem with these threats is the lack of specific signs that a Trojan has entered the computer. Depending on what the infection is supposed to do, you may notice a significant slow-down of your machine’s productivity as well as errors, freezes and, in many cases, BSOD crashes. However, this is not always the case – there may be none of these symptoms. Also, the signs we mentioned may get caused by other issues that aren’t related to a Trojan infection. Still, if anything in your machine makes you suspect that there may be a Trojan inside, be sure to use the guide from and the tool included there to scan and clean your machine.
David Ghost Email Blackmail SUMMARY:
| Name | David Ghost Email Blackmail |
| Type | Trojan |
| Danger Level | High (David Ghost Email Blackmail Trojans are often used as a backdoor for Ransomware) |
| Symptoms | David Ghost Email Blackmail Trojans rarely show visible symptoms and typically hide deep in the system in order to operate in stealth. |
| Distribution Method | Spam messages, phishing emails, infected attachments, fake ads, torrents, illegal websites, cracked software. |
[add_third_banner]
Remove David Ghost Email Blackmail Scam
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to David Ghost Email Blackmail
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the David Ghost Email Blackmail.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and David Ghost Email Blackmail , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – David Ghost Email Blackmail
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to David Ghost Email Blackmail Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
Leave a Reply