About BlueKeep Vulnerability
If you have a Trojan Horse infection named BlueKeep inside your computer, then you should know that your system and all your data are in great danger. The representatives of the Trojans Horse family are very malicious and stealthy threats which typically have the ability to create all sorts of issues. For those of you, who don’t know what to expect from this type of malware, we should say that anything could be expected from a Trojan Horse representative. The Trojans are very versatile pieces of harmful software which can be used equally well in criminal activities like espionage, theft of personal information, system destruction, deletion of files, and even insertion of other viruses in the compromised system like Ransomware or Spyware. That’s why threats like BlueKeep are a favorite tool of many hackers that seek to carry out different cyber crimes. Apart from their multipurpose nature, these pieces of malware have another very nasty feature – they are extremely difficult to detect and can hide deep in the system without showing any particular symptoms for an indefinite period of time. This means that you may not detect anything unusual in the system for a long time, especially if you don’t have a reliable antivirus program which can conduct a full system scan and detect the harmful code that is hiding in the background.
Once they receive a command from the creators, however, the Trojans get activated immediately and reveal their full malicious potential. If not removed on time, malware pieces like BlueKeep Vulnerability could have fatal consequences for your system. That’s why, in the next lines, we will focus on helping you detect and remove the harmful code from your system and save yourself from some unpredictable damage. If you have a trusted antivirus, we would advise you to scan your computer with it. If the antivirus is not able to deal with BlueKeep Vulnerability (yes, sometimes, this malware can block the security program), here we have prepared a removal guide which is specially created to help you remove the nasty Trojan and all of its traces with the help of some detailed manual instructions.
Removing BlueKeep Vulnerability
BlueKeep Exploit is an advanced Trojan-based infection which can sneak inside your system in many ways. Like most other similar infections, this threat uses camouflage to trick the web users about its nature and its purpose and to make them interact with the harmful payload. For that purpose, BlueKeep Virus may present itself as a legitimate-looking message attachment or it could get linked or added to online ads, too-good-to-be-true offers, pirated content and more. One careless click can immediately activate the infection and silently deliver the Trojan into the system. Once it nests inside the computer, this advanced piece of malware can be used for a number of crimes such as theft, espionage, unauthorized access, system resource exploitation, data transmission, banking frauds and more. Unfortunately, it is almost impossible to predict what exactly BlueKeep can do while silently operating in the background of the system because the hackers who are in control can program it for a specific malicious task that serves their criminal intentions. That’s why it is highly recommended to remove such threats as soon as you detect them and not to give them a chance to cause even more harm.
SUMMARY:
| Name | BlueKeep |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | Trojan hide their symptoms very well and usually can’t be detected without reliable security tool. |
| Distribution Method | Spam, fake ads, infected attachments and harmful emails, cracked software, torrents, illegal websites. |
[add_third_banner]
Remove Cve-2019-0708 BlueKeep Vulnerability Exploit
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
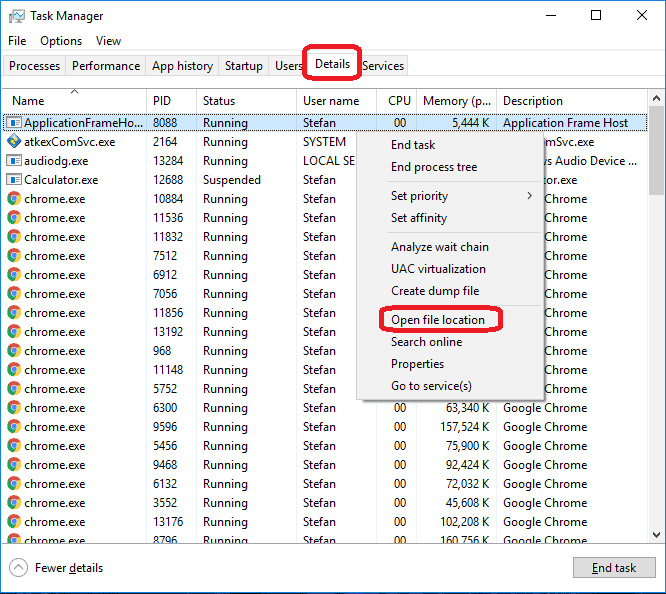
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to BlueKeep
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the BlueKeep.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and BlueKeep , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – BlueKeep
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to BlueKeep Vulnerability. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
Leave a Reply