1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR in depth
A Trojan (or Trojan Horse) is a malicious computer program which is used to infect the targeted computers and initiate various malicious activities in the background of the system. 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR Bitcoin Email Virus is a new representative of this malware category and in the next lines we will tell you more about its behavior and its characteristics. Typically, the Trojan-based programs are used to steal personal information, distribute other viruses or simply disrupt the performance of your computer by deleting important data and corrupting the software in it. In addition, the hackers who are in control can use 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR to gain unauthorized remote access to the infected computer and to exploit its resources without the users’ knowledge. This makes 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR a serious threat to your computer and your data. Once a Trojan horse like this one enters the computer, it typically hides deep in the OS and tries to show no any visible symptoms of its presence. This makes the detection of the infection 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR a difficult task which often requires the assistance of professional security software in order to correctly detect and remove the malware. That’s why you may need to arm yourself with a reliable antivirus program in order to deal with 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR Bitcoin Email effectively. Keep in mind, though, that sometimes 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR may disable the existing security tools in your system in order to prevent its removal. If this is your case and the antivirus that you have is unable to find 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR or deal with it completely, it is extremely important find another way of handling this problem. In the removal guide below, you will find more information on that as well as a trusted scanning tool that can help you locate the nasty Trojan that is hiding in your system.
Removing 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR manually
Many Trojans similar to 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR, 19qqYeGgbzhT8Lic5WsbDZgJkzAy82R6fF , Hoplight are distributed through spam emails, malicious attachments, file sharing platforms and online ads. Once the user interacts with the transmitter, the infection silently installs itself in the system and starts to operate. The activity of each and every Trojan threat depends on the intentions of its author. That’s why we cannot tell you what exactly 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR Bitcoin Email may do inside your PC. However, here are some common actions that can be caused by such threats:
- Infecting, overwriting, hacking, and removing critical system files or formatting system components and installed applications.
- Deleting data from the hard drive
- Blocking the security programs and creating security holes that can be exploited by other malware.
- Distributing computer viruses and threats like Ransomware, Spyware, Rootkits and more.
- Theft of sensitive data, such as credit card numbers, login credentials, passwords, valuable personal documents and other information.
- Tracking the user’s keystrokes and other activities and sending the collected data to remote servers.
- The Trojan horse can also take screenshots and start other activities in the background to steal more information.
- Blocking the users’ access to security resources and sites that provide protection against malware.
- Causing system errors, crashes, unresponsiveness and instability.
If you have 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR on your system or you think that it might be hiding somewhere, it is best to run a full scan with your security software and remove any malicious files that have been detected.
Hi, stranger!
I know the ********, this is your password.
As you can see, I logged in with your account. And I wrote you this message from your account.If you have already changed your password, my malware will be intercepts it every time.
You may not know me, and you are most likely wondering why you are receiving this email, right?
In fact, I posted a malicious program on adults (pornography) of some websites, and you know that you visited these websites to enjoy
(you know what I mean).While you were watching video clips,
my trojan started working as a RDP (remote desktop) with a keylogger that gave me access to your screen as well as a webcam.Immediately after this, my program gathered all your contacts from messenger, social networks, and also by e-mail.
What I’ve done?
I made a double screen video.
The first part shows the video you watched (you have good taste, yes … but strange for me and other normal people),
and the second part shows the recording of your webcam.What should you do?
Well, I think $723 (USD dollars) is a fair price for our little secret.
You will make a bitcoin payment (if you don’t know, look for “how to buy bitcoins” on Google).BTC Address: 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR
(This is CASE sensitive, please copy and paste it)Remarks:
You have 2 days (48 hours) to pay. (I have a special code, and at the moment I know that you have read this email).If I don’t get bitcoins, I will send your video to all your contacts, including family members, colleagues, etc.
However, if I am paid, I will immediately destroy the video, and my trojan will be destruct someself.If you want to get proof, answer “Yes!” and resend this letter to youself.
And I will definitely send your video to your any 11 contacts.This is a non-negotiable offer, so please do not waste my personal and other people’s time by replying to this email.
Bye!
SUMMARY:
| Name | 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | This Trojan typically tries to hide its traces by not showing any visible symptoms of its presence. |
| Distribution Method | Spam, cracked programs, infected email attachments, malicious ads, misleading links, torrents, illegal websites. |
[add_third_banner]
Remove 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR Ransomware Guide
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
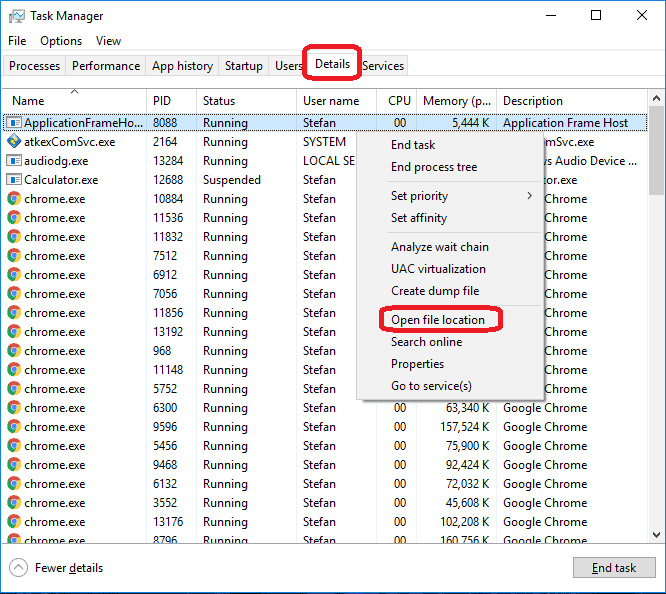
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to 1Q2yu5awJd1Z3UJVw2VckeGoLs6TfSHFQR Bitcoin Email. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
Leave a Reply