About 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS Bitcoin Email
The fact that you are on this page, reading our article about 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS Bitcoin Email probably means that you at the very least suspect that this insidious malware piece may have entered your computer’s system. If that is indeed your current concern, the good news is that you have come to the right site and page as here is where you may find a potential solution to your 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS-related problem. Since this piece of malware is a very dangerous one, acting quickly and without hesitation is very important if you are to save your computer from some very serious damage and negative consequences that may come from the infection. However, before we get to the instructions and the tool that will allow you to redeem your computer from the hazardous 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS, we must first tell you something about this particular malicious program so that you know what you are up against.
Can i Remove 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS Bitcoin Email myself?
If you haven’t bought your first computer yesterday (or even if you have) it is safe to assume that you’ve already heard about the infamous Trojan Horse malware programs. These are nasty and highly problematic pieces of malicious code that the hackers behind them use to complete various criminal tasks inside the computers of their targets. Anything from information theft to damage to the system, from real-time espionage to fully assuming remote control over the attacked machine as well as many many more, are things that a Trojan infection (17jHsGecV53ro2LGzo53s5trTH6Qf3gksS) can be programmed to do or at least help to achieve. Because of the fact that 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS is still a new and not fully researched virus, we do not yet know its exact purpose but we assure you that you must immediately check your computer for it and remove anything that may be related to this threat from your machine’s system.
Is 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS Bitcoin Email Dangerous?
It sure can be annoying when someone starts preaching about how you shouldn’t go to suspicious and sketchy sites or download obscure software but not observing these basic online security rules is precisely what gets many people attacked by Trojans and other malware. And, if you get a Trojan like 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS in your computer, then you may also get a Ransomware cryptovirus (.Moresa, .Verasto, .Norvas) inserted in your system with the Trojan’s help since these malware programs are oftentimes used as tools of distribution for other types of malware such as the nasty Ransomware. Due to all of this, you must indeed not take any chances while in your browser, exploring the online world. There are just too many sketchy sites and unreliable pages as well as infected downloads out there. Just stick to web locations you know and trust and do not open or click on anything that may be a potential security hazard. Also, one last piece of advice from us is to add a reliable antivirus or anti-malware tool to your computer’s protection arsenal. You can even use the suggested security program that we have on this page to help you keep your machine secure.
SUMMARY:
| Name | 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | Normally, a Trojan will show no symptoms but sometimes, if you are lucky, you may notice errors and crashes in your system that may be potential Trojan Horse infection indicators. |
| Distribution Method | Unreliable sites, malvertising and pirated content are the most frequently used methods of spreading Trojans. |
[add_third_banner]
Remove 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS Bitcoin Email Malware
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
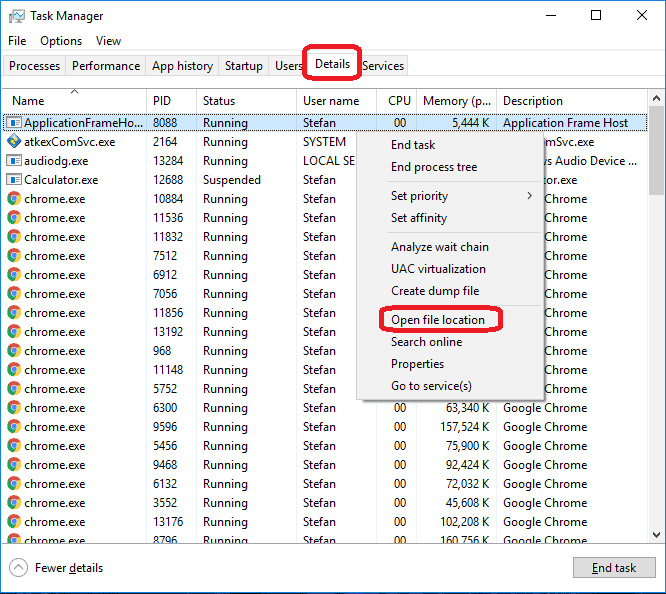
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
Leave a Reply