15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 in Depth
A new web scam campaign has been reported in the recent days and we are determined to inform our readers about it so that they know how to stay safe. The threat this time comes from phishing email scam messages that are created to make you believe that your computer has been compromised by a hidden Trojan Horse. Those messages ( like 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 and 17jHsGecV53ro2LGzo53s5trTH6Qf3gksS ) follow a basic scenario where a self-proclaimed hacker claims that they have gained access to your passwords, to some sensitive personal information or to important system controls and that if you don’t pay them a certain amount of money in ransom, they will do something bad to your machine or with your data. Typically, the ransom is requested in BitCoin and needs to be paid to a given cryptocurrency wallet. Unfortunately, apart from scaring you, sometimes, such scams may contain an actual real Trojan Horse, such as 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6, or another malware which may indeed harm your PC in a really bad way. That’s why it is not a good idea to simply ignore them in case you have recently been bombarded with some emails with similar content, especially if you have interacted with their contents.
How Dangerous is 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6?
In fact, since you are on this page, we will suggest you carefully scan your computer with a reliable antimalware tool (if you don’t have one you can use the program that has been suggested below) and take the necessary actions to remove any malicious or suspicious components that get detected in your system. The reason is, there are thousands of nasty computer threats that can sneak into your PC after you interact with the contents of some unsafe spam email and that is also how you may end up with 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 in your computer. This threat, in particular, is extremely stealthy and difficult to detect. As a typical Trojan-based infection, 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 is also multi-functional which means that its criminal creators can use it for all sorts of nasty actions. They may weaken the security of your system by blocking your security programs with its help, mess with the software and the data that you store on the computer, delete your files, modify and replace your programs and even install new malicious apps without your knowledge. In theory, 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 may be capable of spying on you or stealing your passwords and banking details and providing the hackers with remote access to your machine. That’s why it is not excluded that you may receive different scam and blackmailing messages from the crooks behind the virus, which is why the first thing you should do if you’ve been receiving sketchy blackmailing e-mails would be to rule out this possibility.
Can I remove 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 myself?
Of course, we need to mention that there are hundreds of online scams and spam email messages out there and, in most of the cases, the statements made in the blackmailing letters are fake. That’s why you should not get too stressed about them and, most importantly, never send your money to anyone who’s blackmailing you in such a way. Instead, use a trusted scanner to check your machine. In case the scan detects 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 on your PC, below you will find a detailed removal guide and a trusted removal tool which are both good options that can help you remove this nasty malware in a safe and reliable manner.
I got full access to your email account and sent it from there! Few months ago I infected your computer with mine private malware ( Remote Administration Tool ) your browser wasn’t patched. My tool gave me full control over your computer, even your microphone and webcam. I collected all the interested things I have found on your computer, your pictures, your whole privacy you dirty pervert! I even recorded some video of you, over your webcam, you know what I mean!!! I give you the chance to pay me, exactly: 700$ in bitcoin, or I will publish all I got from you, on social network, messenger, and I will everyone else know about everything I got from you! Compared to the damage and hell it will bring into your life, I think its a very good price! You can register your bitcoin wallet here: login.blockchain.com To get bitcoin, search “Where to buy bitcoins?”. My bitcoin adress is: 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6
15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 SUMMARY:
| Name | 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 |
| Type | Trojan |
| Danger Level | High ( 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 Trojans are often used as a backdoor for Ransomware) |
| Symptoms | 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 Normally, a Trojan will show no symptoms but sometimes, if you are lucky, you may notice errors and crashes in your system that may be potential Trojan Horse infection indicators. |
| Distribution Method | Unreliable sites, malvertising and pirated content are the most frequently used methods of spreading Trojans like 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 |
[add_third_banner]
Remove 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 Bitcoin Email Virus
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
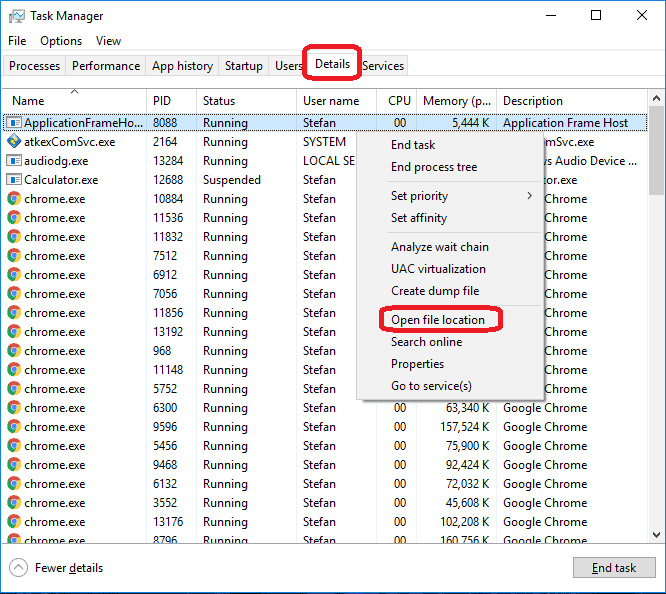
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to 15w8KYwC76vDRiSZD2LK6dEbHvs7N38mh6 Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
Leave a Reply