The .Madek Virus in Depth
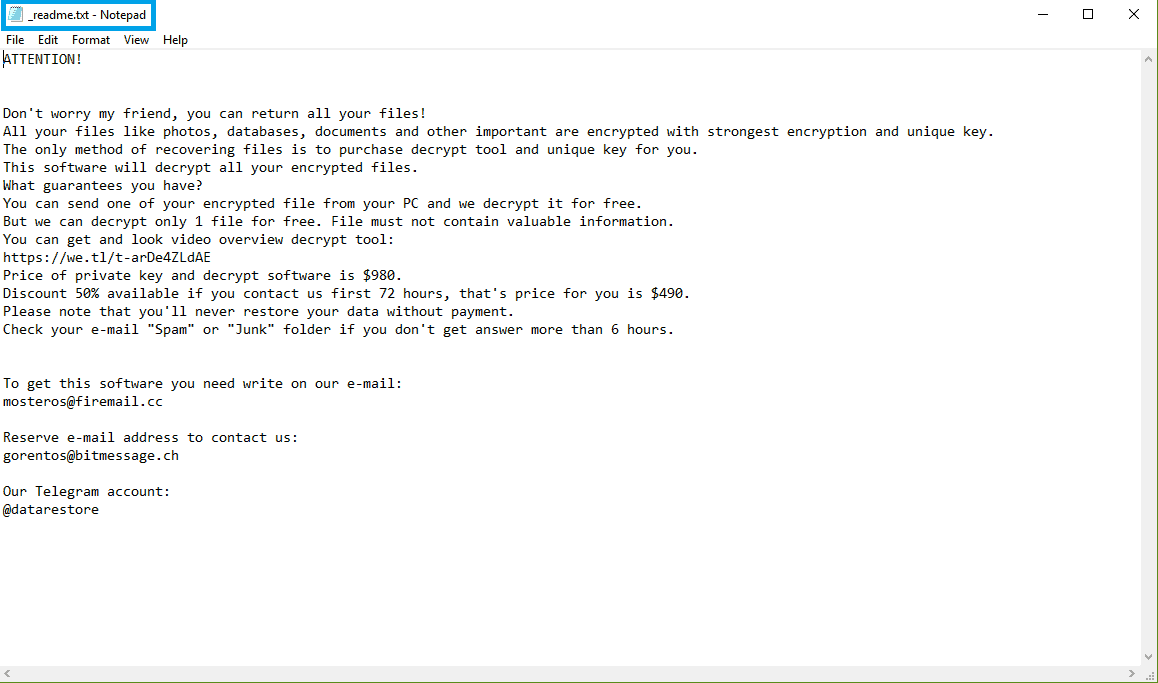
What is Madek Ransomware, how does it work and how can you fight it? If this is the question that has brought you to “How to remove guide”, then you are in the right place. Madek is a recently reported cryptovirus infection, which can silently encrypt all of your personal files in order to ask for a ransom for their decryption.
Although the vast majority of criminal groups are changing to banking Trojans, those who stick to Ransomware infections like this one are improving their blackmailing strategies. We are not talking about a new phenomenon, but over time, the infections of this type have significantly improved and are currently a huge issue to many web users.
Think of Madek as a blackmailing tool – just like most Ransomware threats, this one is a form of malware that, once it takes over your computer, blocks the access to your data. And, once the user’s data gets locked up so that the victim can’t open it, the attacker who is in control of the infection demands a ransom from the victim and promises to restore the access to the blocked data once the payment is made.
Ransomware is always evolving. With new and sophisticated variants such as Madek, Adame or Budak it poses new threats for both companies and individual web users. One of the most common ways of distribution is through email spam. The malware usually hides in attachments that reach the victim in an email, which resembles a file they should trust. Other methods of distribution include illegal websites, malicious links, malvertising, and cracked software installers. Therefore, apart from using reliable security software, the web users should always be mindful of the type and the origin of the web content they interact with.
Is it a good idea to pay the ransom for an encrypted .Madek file

We agree to the commonly given advice by most researchers and experts in the field paying the ransom requested by the criminals is not a good idea and you shouldn’t go for that. Sadly, even if you pay and fulfill all of the hackers’ demands, there is absolutely no guarantee that they will restore your files and everything will get back to normal. That’s why it is a good idea to focus on removing Madek and then trying out some alternative methods you can use to restore your files. For instance, you can use your personal backups or give a try to the file-recovery instructions in the removal guide below. Obviously, we cannot tell you how likely it is that you will recover all of your data but we can at least help you to remove the infection and make your computer safe again.
When it comes to preventing any malware attacks, knowledge is the key. Since email spam is the most popular method of distribution for Ransomware, you must be very careful with what emails you open and what files you download. You should also consider investing in reliable anti-virus software. One that is capable of blocking the Ransomware so that it stops the infection before the encryption even begins. The third and VERY IMPORTANT thing is to create backup copies of your data on a regular basis. It is important to use an external drive or a cloud storage that includes high-level encryption and multi-factor authentication. But above all, use your common sense. If something seems suspicious, it probably is, and you should avoid it.
SUMMARY:
| Name | Madek |
| Type | Ransomware |
| Danger Level | High (Ransomware is by far the worst threat you can encounter) |
| Symptoms | Very few and unnoticeable ones before the ransom notification comes up. |
| Distribution Method | From fake ads and fake system requests to spam emails and contagious web pages. |
[add_third_banner]
Remove the .Madek Ransomware
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to Madek
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the Madek.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and Madek , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – Madek
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to Madek Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
7: Madek Decryption
The previous steps were all aimed at removing the Madek Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them. For that, we have a separate article with detailed instructions on what you have to do in order to unlock your data. Here is a link to that guide.
Leave a Reply