About .Help File Virus Ransomware
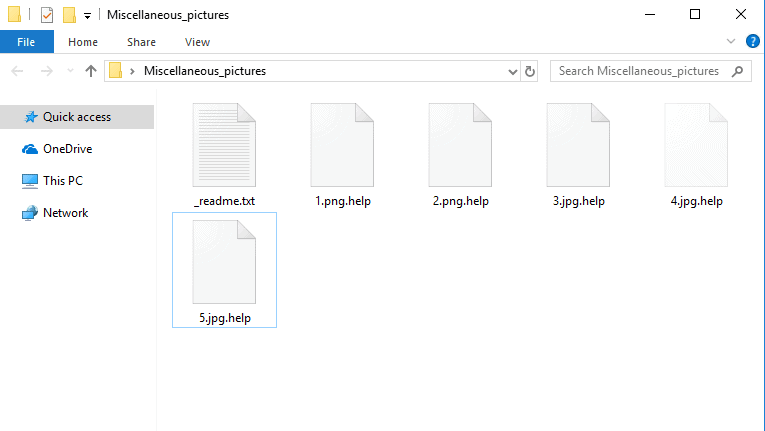
After the ransomware encrypt your files, it leaves a _readme.txt file as a message for the user with instructions to follow:
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail [email protected]
Write this ID in the title of your message 1E857D00-1016
In case of no answer in 24 hours write us to this e-mail:[email protected]
If there is no response from our mail, you can install the Jabber client and write to us in support of [email protected]
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 10Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price.
hxxps://localbitcoins.com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
hxxp://www.coindesk.com/information/how-can-i-buy-bitcoins/
Jabber client installation instructions:
Download the jabber (Pidgin) client from https://pidgin.im/download/windows/
After installation, the Pidgin client will prompt you to create a new account.
Click “Add”
In the “Protocol” field, select XMPP
In “Username” – come up with any name
In the field “domain” – enter any jabber-server, there are a lot of them, for example – exploit.im
Create a password
At the bottom, put a tick “Create account”
Click add
If you selected “domain” – exploit.im, then a new window should appear in which you will need to re-enter your data:
User
password
You will need to follow the link to the captcha (there you will see the characters that you need to enter in the field below)
If you don’t understand our Pidgin client installation instructions, you can find many installation tutorials on youtube – hxxps://www.youtube.com/results?search_query=pidgin+jabber+install
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
In case you wish to get more info in relation to a newly developed computer virus program called .Help, the next paragraphs could provide you with some vital and helpful information about the malicious software. The malicious virus that’ll be the focus of the next lines is what experts describe as Ransomware. This virus class carries the unique ability to use the so-called file-encryption technique, by means of which the Ransomware virus programs like (.Help, .Rezuc .Skymap, .Rectot, .Mogera)have can take hostage the private documents of the targeted victim, thus making the data inaccessible. Cryptoviruses such as .Help would, in most cases, generate a notification or a notepad file that serves the purpose of demanding a ransom money payment from the Ransomware victim. The online hackers also typically include exhaustive guidelines within the dreaded ransom notification message that the virus’ victim has to comply with in order to correctly carry out the requested ransom transfer. In addition, the victims are oftentimes told that if the requested ransom money doesn’t get transacted on time or in full, the online hackers controlling this horrible computer virus would not restore the access to the encoded software data. In case you’re one of the countless customers that have had the misfortune of landing .Help on their computer, it’s highly advisable that you get well informed regarding all the characteristics associated with the Ransomware viruses which is the reason we suggest that you continue reading.
What you need to know about the payment demanded by the online criminals
In case some of our readers are thinking about executing the requested ransom transaction, we shall examine everything that comes with it so as to enable you to make the best decision for your case.
The blackmailers who have unleashed this type of nasty threat upon your PC are solely after your money – they couldn’t care less about you or about your encrypted computer documents. Needless to say, as you may assume, the ransom money is usually supposed to be transacted following certain specific requirements and conditions. Generally, such a condition is the implementation of Bitcoins as a payment currency. A well-known trait of the bitcoin cyber-currency is the fact that it is mostly untraceable. Therefore, it should not be hard to realize why the online criminals wish that the ransom is transacted through the use of this sort of cryptocurrency. Sadly, the use of Bitcoins is amongst the key things that enable nearly all Ransomware hackers to remain unpunished for their crimes.
Can I Remove Myself .Help File Virus?
There’s also the troubling potential for transacting the ransom money and still not getting the locked-up file documents restored. Due to this, the thing we would suggest in instances where a Ransomware has gotten hold of your files is to assess all potential alternative options and ways to handle the issue and try them all, leaving the money payment as a last resort option. One important thing that we advise you to do in case your documents have been locked and taken hostage by the nasty cryptovirus would be to have a look at our manual guide you will see below this paragraph and carry out its guidelines because it may help you handle this issue.
.Help SUMMARY:
| Name | .Help |
| Type | Ransomware |
| Danger Level | High (.Help Ransomware encrypts all types of files) |
| Symptoms | .Help Ransomware is hard to detect and aside from increased use of RAM and CPU, there would barely be any other visible red flags. |
| Distribution Method | Most of the time, Trojans get distributed through spam e-mails and social network messages, malicious ads, shady and pirated downloads, questionable torrents and other similar methods. |
[add_third_banner]
Remove .Help File Ransomware Virus
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to .Help
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the .Help.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and .Help , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – .Help
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to .Help Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
7: .Help Decryption
The previous steps were all aimed at removing the .Help Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them. For that, we have a separate article with detailed instructions on what you have to do in order to unlock your data. Here is a link to that guide.
Leave a Reply