About the Format Virus
In this post, we shall concentrate on one very noxious piece of software labeled Format giving you all the necessary details that you should know about it. The harmful software program that we’ll be focusing on here belongs to the category of Ransomware virus programs for example Ndarod, Bopador or Access. What you must bear in mind with regards to Ransomware such as Format is the fact that most malware viruses of this category usually apply file encryption on the personal files of the victim as a way to extort money out of them. Once the file encryption process has completed, the user is greeted by an unpleasant ransom notification message where the cyber criminals explain to the targeted user that if they want their data decrypted, they would have to transfer a set amount of money in exchange for the decryption code. Most of the time, there will also be instructions inside the pop-up that are supposed to guide the user through the process of carrying out the ransom payment. Additional threats that may be contained in the ransom message might inform the targeted individual that the unwillingness to pay the required ransom might lead to a total loss of the encrypted files.
What to do with the .format files?

A key aspect regarding computer viruses of this kind is that Ransomware is not like other, more usual forms of malware. The kind of malware you have caught is designed to lock up your personal computer files without actually doing any harm to any of the components of your system. Even though it may not seem like that, file encryption is actually a procedure that is primarily used for data defense and isn’t harmful on its own. The key reason why this is so crucial is that, given that no actual harm is done by the Ransomware, detecting the virus invasion can be really tricky and the noxious infection is generally capable of staying under the radar of both the user and their anti-virus program. We regret to tell you that there aren’t a lot of instances where users have managed to recognize the PC virus on time and to stop its task before it has become too late. Another reason for this is the fact that the potential signs or symptoms of the infection (especially with Format) are oftentimes almost undetectable.
Without doubt, lots of you have come to this page since the highly malicious Format has sealed your documents. If this is your case, you will find a special Format Ransomware removal guide down below which could assist you in handling your issue and recover your files.
All this stealthiness is because the typical Ransomware blackmailing scheme could only get the job done if the attacked users feel frightened and surprised by the ransom message. The crooks rely on fear and frustration to make the victims pay as soon as possible without giving them time to seek alternatives. That is why, if you want to overcome a virus attack such as Format, it is crucial to get well aware of and search for other options rather than reacting out of fear and anxiety and paying what the criminals want from you.
SUMMARY:
| Name | Format |
| Type | Ransomware |
| Danger Level | High (Ransomware is by far the worst threat you can encounter) |
| Symptoms | Very few and unnoticeable ones before the ransom notification comes up. |
| Distribution Method | From fake ads and fake system requests to spam emails and contagious web pages. |
[add_third_banner]
Format Ransomware Removal
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to Format
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the Format.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and Format , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – Format
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to Format Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
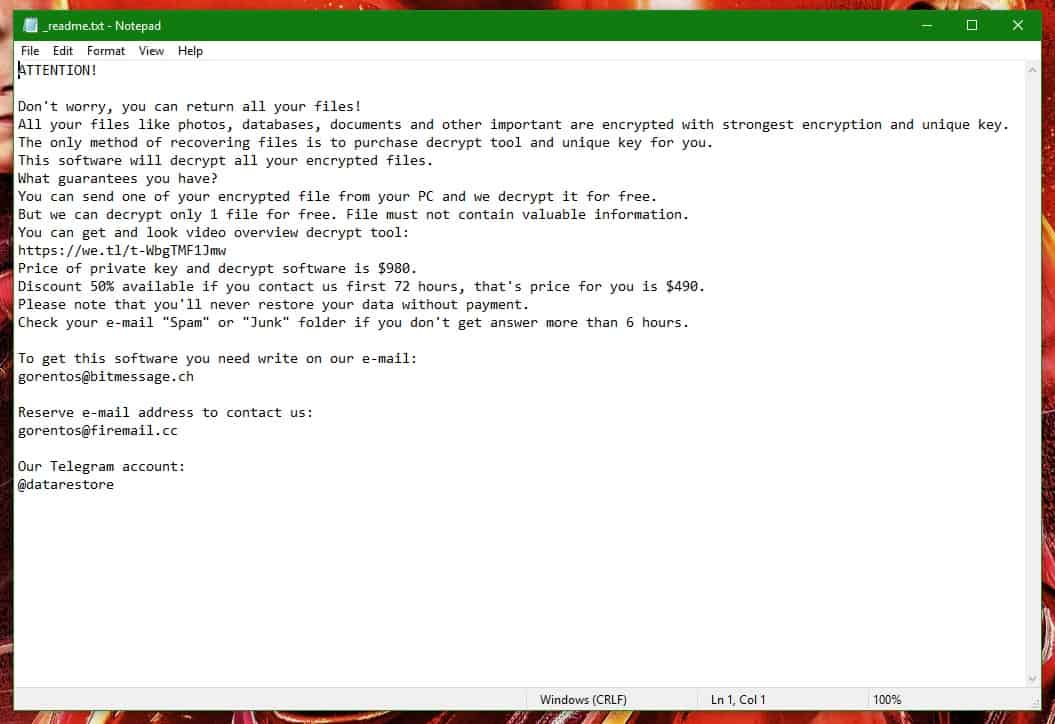
7: Format Decryption
The previous steps were all aimed at removing the Format Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them. For that, we have a separate article with detailed instructions on what you have to do in order to unlock your data. Here is a link to that guide.
Leave a Reply