If your computer has recently become sluggish, plagued by flickering windows, or interrupted by unexpected pop-ups, the culprit may be a Trojan known as PDFast.exe. This threat has drawn attention from users reporting strange activity tied to the suspicious PDFast process. After analyzing its behavior, it has been classified as Trojan Horse malware – a deceptive type of malicious software that appears legitimate while secretly performing harmful tasks. Once on a system, PDFast can consume significant resources, alter system settings, and compromise sensitive information such as credit card data through phishing and keylogging. It commonly enters machines via bundled software downloads, then reinforces its presence by modifying the Windows Registry, creating additional files, and scheduling tasks that make removal difficult. While manual removal is possible, the process is complex and time-intensive for most users. This guide provides clear, step-by-step instructions to help you detect and fully remove the PDFast Trojan.
What Is the PDFast Virus?
Trojans are malicious programs disguised as legitimate software to trick users into installing them, often resulting in serious security breaches. Their primary purpose is to create unauthorized access to a system, enabling attackers to steal data, monitor activity, or deploy additional malware.
Once installed, a trojans like PDFast and Kepavll typically exhibits traits such as hiding within common files, running silently in the background, and avoiding detection by security tools. A particularly dangerous aspect of PDFast is its ability to gain administrative privileges, allowing it to override system settings, disable antivirus programs, and open the door to full system control.
PDFast also runs unauthorized processes, some of which appear to be legitimate system services, making them difficult to identify.
Additionally, certain variants of PDFast hijack CPU and memory resources to mine cryptocurrency, causing significant performance issues and higher energy consumption. These hidden operations can go unnoticed for long periods, increasing potential damage.
How to Remove the PDFast Virus
Based on our in-depth research and extensive experience with similar threats, we’ve developed a detailed guide to help you completely remove the PDFast Trojan. If you’re confident in your troubleshooting or virus removal skills, feel free to skip directly to the summary section, where we outline all the necessary steps.
PDFast Manual Removal Steps Overview
- Preparatory Steps: Easy – Preparatory Steps: Start by making hidden files visible on your system and installing LockHunter.
- Task Manager Cleanup: Moderate – Task Manager Cleanup: Identify suspicious processes in the Task Manager, terminate them, and delete their source files.
- Delete Remaining PDFast Files: Moderate – Delete Remaining PDFast Files: Search directories like AppData, Roaming, and Temp for leftover malware data.
- Delete Startup Items: Easy – Check your Startup apps and disable anything strange or unwanted.
- Delete Scheduled Tasks: Moderate – Delete Scheduled Tasks: Look in Task Scheduler for tasks related to the malware and remove them.
- Registry Cleanup: Hard – Registry Cleanup: Locate and erase malicious Registry entries associated with PDFast.
If this summary feels too brief or you’re not confident proceeding, refer to the complete set of instructions below for a detailed breakdown.
Removal Methods at a Glance
| Threat Name | PDFast |
| Threat Type | Trojan Horse/Malware |
| Threat Level | High (Trojans exploit system resources, run harmful processes, collect sensitive data, distribute other malware, etc.) |
| Removal Methods: | – |
| ➣ Manual Method – Advanced Steps | 40-60 minutes – high success rate |
| ➣ Automatic Method – SpyHunter 5 | 5-10 minutes – very high success rate |
How to Get Rid of PDFast – Full Guide
Below is the step-by-step tutorial to walk you through the manual removal of PDFast. If you’re ready to handle this manually but need guidance, this section is for you.
1. Preparatory Steps
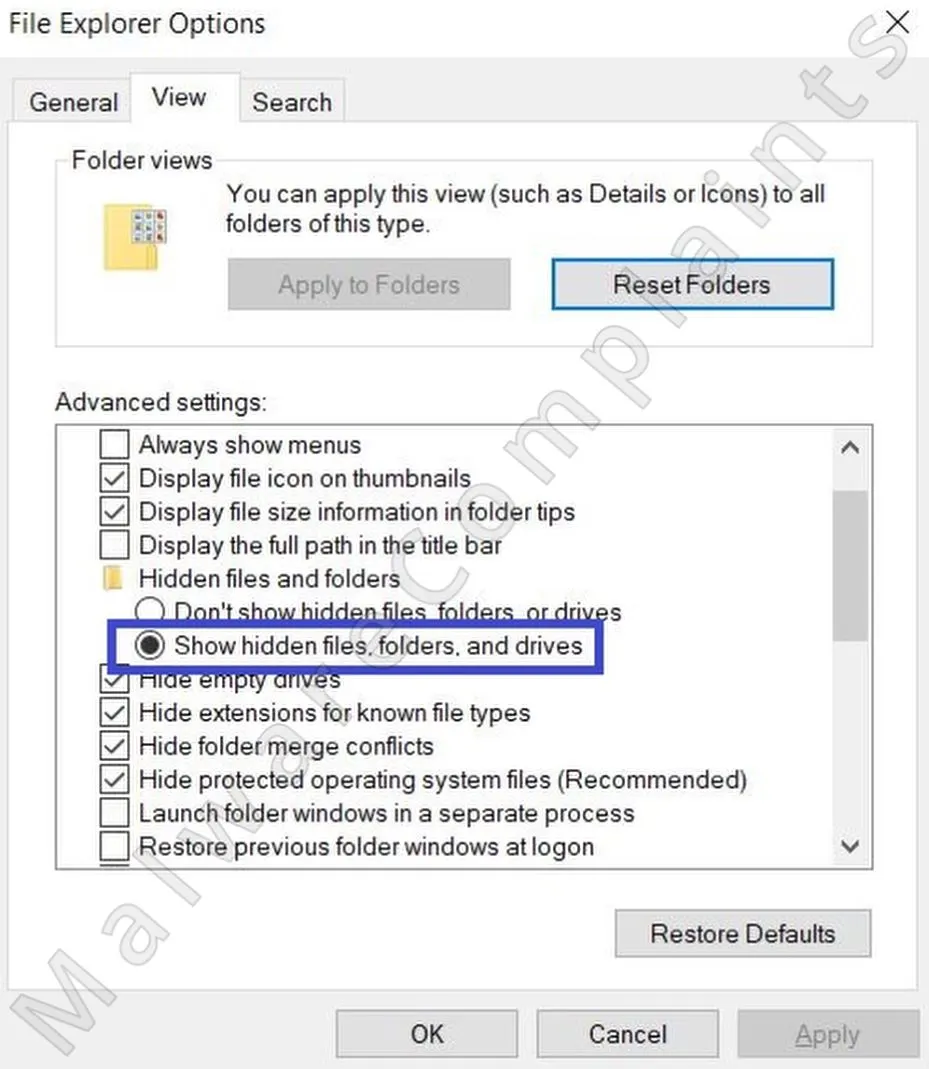
- 1.1Though the bulk of this removal process will be handled manually, there’s one handy tool you’ll need to install first. The application is called LockHunter, and it plays an important role in removing files that the malware attempts to lock or protect from deletion.
2. Get Rid of Rogue Processes in the Task Manager
- 2.3If you come across a suspicious process, right-click it and choose Open File Location. Minimize the folder that appears. Then, return to Task Manager, select the same process, and click End Task.
- 2.4Go back to the minimized folder window and erase all files contained there.
3. Delete Remaining PDFast Files
- 3.1You’ll now need to comb through the following directories to look for files or subfolders with names that seem out of place or potentially harmful:
– C:\Users\[Username]\AppData\Local
– C:\Users\[Username]\AppData\Roaming
– C:\Users\[Username]\AppData\Local\Temp
– C:\Users\[Username]\AppData\LocalLow
– C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
– C:\Users\[Username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
– C:\Program Files
– C:\Program Files (x86)
– C:\ProgramData - 3.2Remove anything that seems dubious. These folders generally don’t hold essential system files, so deleting something unintentionally safe will likely just affect a specific program—which can easily be reinstalled. Once inside the Temp directory, feel free to delete every file.
4. Disable PDFast Startup Items
- 4.1Head back to Task Manager and open the Startup tab. Disable any entries that look unfamiliar or suspicious.
- 4.2Keep enabled only the programs that you recognize and actually want to launch when the system starts up.
5. Eliminate PDFast Scheduled Tasks
- 5.2Review all listed tasks carefully. Select each task one at a time, switch to the Actions tab, and examine what command or file the task is configured to run.
- 5.3If any task appears to launch an odd-looking .exe or script file, go ahead and delete that task.
6. Remove PDFast Items From the Registry
- 6.1To launch the Registry Editor, open the Start Menu, type regedit, and run the top result as an administrator.
- 6.2Once inside, press Ctrl + F, type PDFast, and begin searching. Delete any entries found on the left-hand panel and keep searching until no results remain.
- 6.3If a certain key refuses to be removed, right-click it, choose Permissions, go to Advanced, then select Change. Type Everyone, confirm with OK, and try deleting it again.
- 6.5Within each of these directories, check the right-hand panel for entries with suspicious names. If you discover anything unusual that might be associated with PDFast, delete those values. Be sure not to delete the entire key (the folder in the left pane) where the value resides—only remove the specific suspicious entries.

Leave a Reply