About 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK
The Trojan Horses malware programs are known to be highly stealthy malicious pieces of software that can attack any computer without making their presence known. If you are on this page because you think your system may have been targeted and invaded by a nasty Trojan Horse known as 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK Bitcoin Email, then, at the very least, you are a bit closer to solving the infection issue you may have on your hands. After all, most users do not even suspect that their computers have been attacked by a Trojan Horse representative which is what makes these insidious programs so problematic. However, now that you are here, you will have access to a set of instructions and also to a trusted anti-malware tool, both of which can be of great use in the battle against the nasty 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK. Before we show you the removal steps in our dedicated 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK removal guide, however, we must first briefly introduce you to the threat that you are facing. 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK is more than some annoying malware program that you can ignore – quite the contrary. It is a sophisticated and dangerous Trojan Horse virus and it may be used in various ways as long as it pushes forward the agenda of its anonymous creators. And that agenda could be anything – the hackers using this malware may be seeking to steal sensitive information from the machines of their victims and then blackmail them using the collected data as leverage. They may also employ the Trojan as a backdoor tool and then insert an additional malware such as a Ransomware cryptovirus that can seal the files of the user through means of encryption and keep them locked until the user transfers a ransom payment. Some Trojans are also known as highly advanced Spyware tools that can live-monitor their victims without any visible symptoms of the infection. All in all, a very nasty infection that needs to be taken care of ASAP.
Removing 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK manually
The examples that we provided regarding the potential forms of damage and harassment that may come from a Trojan like 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK Bitcoin Email are only a small portion of all the nasty abilities that these threats can be programmed to possess. One of the main traits of the Trojan infections in general is that they can be quite unpredictable. In fact, if you have noticed anything suspicious in your system that has lead you to the conclusion that your machine may have been infected, you can consider yourself lucky. In most cases, there won’t be any visible indications that would alert the user to the malware’s presence in the system. And, if we are talking about a new threat like 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK, .Moresa , .Norvas then even an antivirus program may not detect it due to outdated virus definitions.
Once you finish the guide and hopefully remove 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK, be sure to provide your computer with good protection in the future. Never leave your PC without a good security tool (if you have no such tool, check out the one we’ve linked in this article). Also, never download any sketchy programs or ones that are pirated and be sure to keep away from spam message attachments, phishing pages, unreliable sites and invasive web ads as those could all land you nasty malware programs like the one we’ve just talked about.
Hello!
I’m is very good programmer, known in darkweb as sanson10.
I hacked this mailbox more than 3 months ago,
through it I infected your operating system with a virus (trojan) created by me and
have been spying for you a very long time.I understand it is hard to believe, but I have full access to your account:
You can check it yourself, I’m wrote you from yours account!Even if you changed the password after that – it does not matter, my virus
intercepted all the caching data on your computer
and automatically saved access for me.I have access to all your accounts, social networks, email, browsing history.
Accordingly, I have the data of all your contacts, files from your computer, photos
and videos.I was most struck by the intimate content sites that you occasionally visit.
You have a very wild imagination, I tell you!During your pastime and entertainment there, I took screenshot through the camera of
your device, synchronizing with what you are watching.
Oh my god! You are so funny and excited!I think that you do not want all your contacts to get these files, right?
If you are of the same opinion, then I think that $637 is quite a fair price to
destroy the dirt I created.Send the above amount on my BTC wallet (bitcoin): 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK
As soon as the above amount is received, I guarantee that the data will be deleted,
I do not need it.Otherwise, these files and history of visiting sites will get all your contacts from
your device.
Also, I’ll send to everyone your contact access to your email and access logs, I
have carefully saved it!Since reading this letter you have 48 hours!
After your reading this message, I’ll receive an automatic notification that you
have seen the letter.Please do not try to answer me, the from-address is generated automatically!
I hope I taught you a good lesson.
Do not be so nonchalant, please visit only to proven resources, and don’t enter your
passwords anywhere!
Good luck!
SUMMARY:
| Name | 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | In some instances, an infection like 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK may trigger errors and crashes in your machine which could give away the malware. |
| Distribution Method | Unreliable websites, phishing pages, pirated programs, malvertising and others. |
[add_third_banner]
Remove 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK Bitcoin Email Virus
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
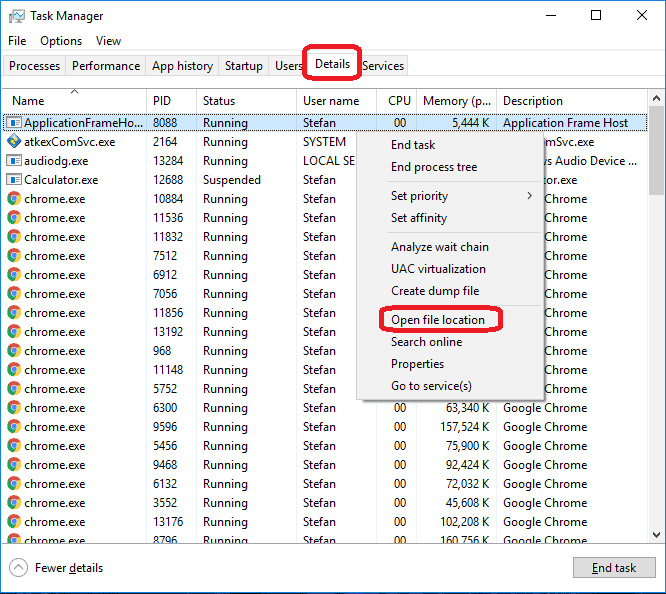
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to 1BVVqiqX1mAVNujniRgi2NBopqA6HmZgtK. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
Leave a Reply