.Kvag
Kvag is a Ransomware infection with very malicious file-encrypting capabilities. The Kvag infection can blackmail you to pay a ransom in exchange for regaining the access to your personal files.
In case you have been blocked from accessing your documents, images, and other important data, and a scary ransom note has asked you to pay some money to regain that access, then you have definitely become a victim of this threat, and would like to learn how to remove it.
There’s a solid reason to be scared of this malware, because this is one of the latest cryptoviruses that comes packed with highly malicious abilities. If we have to compare it with other malicious threats like Trojans, Spyware or Viruses, this malware acts in a very special way. The Ransomware uses a unique encryption code, that does not destroy your files, or your system like most other malware types do. This means you will not have your data corrupted, or destroyed if you fall a victim to this virus, but it will be locked with a powerful, and almost unbreakable algorithm. The method of encryption is used by the malicious actors behind the Ransomware to blackmail you for the release of your personal files.
Unfortunately, this illegal money-making scheme has rapidly evolved into a lucrative “business” model for different hacking organizations, and every day they come up with new and more advanced threats of this kind. The victims are promised to obtain a decryption key for their documents if they pay a certain amount of money, but there is really no assurance that they will receive one. And this is the worst aspect of being a victim of a threat like Kvag, Meds and Moka – the uncertainty.
The .Kvag virus
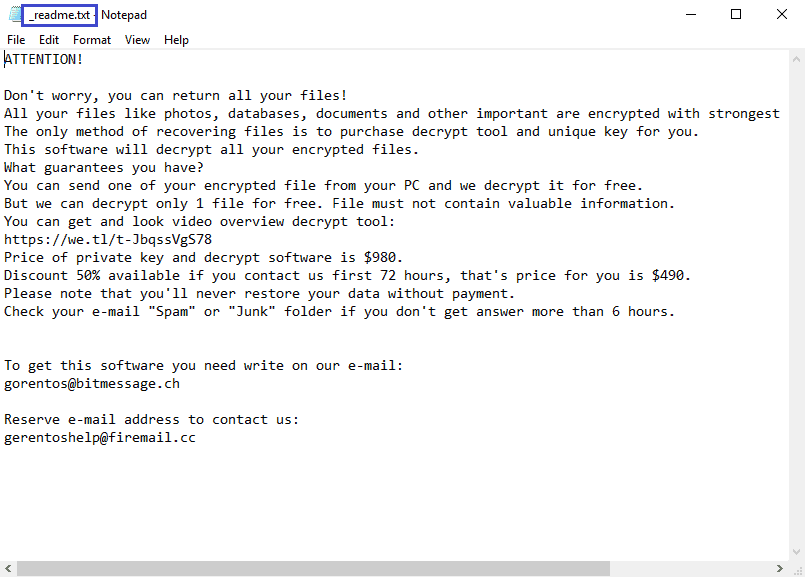
The Kvag virus is a very stealthy infection. It is almost impossible to detect the Kvag virus since it hides well in the system, and rarely shows visible symptoms.
The moment the malware sneaks inside the computer it begins to encrypt the information instantly, but there are hardly any visible symptoms that could indicate what’s going on. The cryptovirus reveals itself only when the entire process of encryption gets completed. The hackers place a ransom-demanding note on the screen, they may replace your desktop background with it, and even place it in every folder that contains encrypted files. Some ransomware variants even play an audio file, explaining to you what has happened to your files. All this is done just to panic, and prompt the victims to make the payment as soon as possible.
The .Kvag file encryption

The Kvag file encryption is what keeps your files inaccessible. Decrypting the Kvag file encryption can be very challenging, and is typically possible only with the help of the corresponding decryption key.
You’ve probably heard, though, that many reputable security experts warn that paying the ransom required for the decryption key might be the worst course of action you might take. This is because, in a lot of cases, the hackers don’t really send a decryption key to the victims once they pay. That’s why it is advisable to take the initiative into your own hands, and remove Kvag by following the instructions in the guide below, instead of risking your money.
SUMMARY:
| Name | Kvag |
| Type | Ransomware |
| Danger Level | High (Ransomware is by far the worst threat you can encounter) |
| Symptoms | Very few and unnoticeable ones before the ransom notification comes up. |
| Distribution Method | From fake ads and fake system requests to spam emails and contagious web pages. |
[add_third_banner]
Remove Kvag Virus Ransomware
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.

Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to Kvag
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the Kvag.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and Kvag , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – Kvag
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to Kvag Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
7: Kvag Decryption
The previous steps were all aimed at removing the Kvag Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them. For that, we have a separate article with detailed instructions on what you have to do in order to unlock your data. Here is a link to that guide.
Leave a Reply