If you are one of thousands of users to receive an email about “Cisco router, vulnerability CVE-2018-0296“, please be aware that it is infected with a Trojan horse. Feel free to read more about it and use our removal guide (second half of the article) in case you have opened it.
A Trojan Horse virus infection is certainly one of the last things that you’d like to happen to your computer and yet you are on this page which most likely means that your machine has already gotten invaded by a scary email “Cisco router, vulnerability CVE-2018-0296” and that you are now seeking help with removing it. More then 6 thousand abuse cases have been found so far. Now, Trojans are definitely some of the worst forms of malware programs that can attack your computer and there are many reasons for that – those viruses are really stealthy, difficult to spot and locate inside the infected machine and their potential capabilities are many meaning that a single piece of Trojan Horse malware could be used to carry out a number of harmful activities inside a targeted computer.
Update: Many users have pointed out in the comment section that the email they have received includes old passwords. We suspect that they could have been obtained from an older hack of one of the major websites out on the Internet. We advise you to set new passwords on all your important accounts. Especially vulnerable are families and businesses, as it is hard to locate the source of the problem.
That being said, you should still not despair even if the malicious “Cisco router, vulnerability CVE-2018-0296” (or some other Trojan) has managed to infiltrate your computer – there are still things you can do to counteract the infection and in the lines below, we will try to show you the most effective methods of eliminating this virus and making your PC safe for further use.
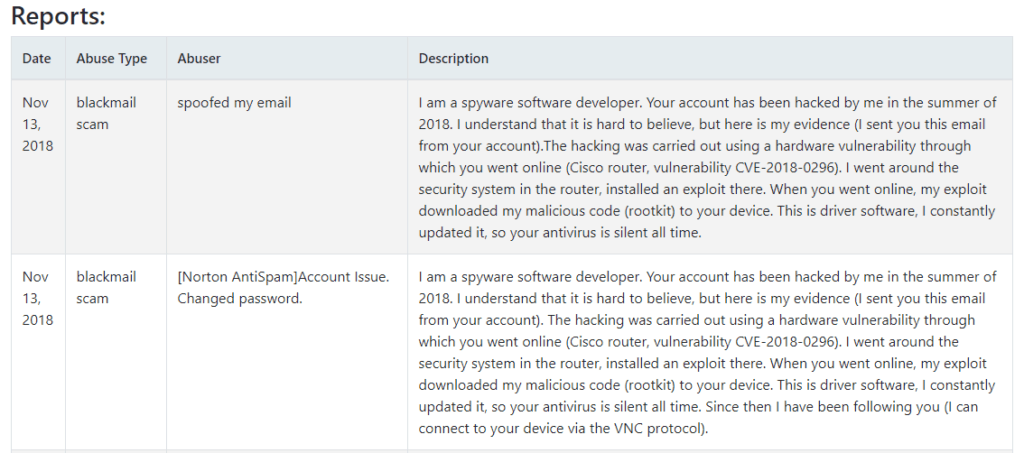
I am a spyware software developer. Your account has been hacked by me in the summer of 2018. I understand that it is hard to believe, but here is my evidence (I sent you this email from your account).The hacking was carried out using a hardware vulnerability through which you went online (Cisco router, vulnerability CVE-2018-0296). I went around the security system in the router, installed an exploit there. When you went online, my exploit downloaded my malicious code (rootkit) to your device. This is driver software, I constantly updated it, so your antivirus is silent all time.
What to expect with a Trojan on your PC
We already said that those threats could be really versatile and that this one of the main factors that make them so dreadful. A Trojan virus the likes of “Cisco router, vulnerability CVE-2018-0296” very similar to Win32/Wajagen.a which hit the internet last week. Scan be used for system corruption, deletion and theft of personal data, espionage, distribution of more malware (Spyware, Ransomware, Rootkits, etc.) and so on and so forth. In general, it’s difficult to predict the actual purpose of a given Trojan Horse attack exactly because of the wide variety of activities that this type of malicious programs could execute. The important thing in all instances of a Trojan Horse invasion, however, is to waste no time and eliminate the noxious program before it gets too late.
Further protection and some more facts about the Trojan Horse malware class
You can use the guide above and/or the anti-malware program we’ve added to it to try and remove “Cisco router, vulnerability CVE-2018-0296” but even if you successfully eliminate the infection, this doesn’t mean you should let your guard down. These threats are really widespread and that is why you must constantly be on the lookout for anything that could land you another similar virus. Usually, Trojans are disguised in some way that allows them to reach more users without getting recognized as malware – spam message/e-mail attachments, pirated programs distributed via sketchy sites, fake web requests, download offers and random misleading links as well as many other kinds of content can be used for spreading “Cisco router, vulnerability CVE-2018-0296” and other similar infections. Be sure to avoid all of those as well as anything else that might not be safe or else your machine might get infected as well.
Also, note that Trojans normally show very very few (if any) infection symptoms and so it’s a good idea to have a good antivirus at your disposal that can help you detect and maybe stop a potential Trojan attack in case there are no visible signs of the malware’s presence on your computer.
SUMMARY:
| Name | Win32/Wajagen.a |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | Most of the time there won’t be any symptoms yet, still, if you notice any weird system behavior be sure to investigate further as it might as well be caused by a Trojan Horse infection. |
| Distribution Method | Most of the time, Trojans get distributed through spam e-mails and social network messages, malicious ads, shady and pirated downloads, questionable torrents and other similar methods. |
[add_third_banner]
Cisco router, vulnerability CVE-2018-0296 Trojan Removal Guide
Within the next guide, you will be given instructions that will help you remove the Cisco router, vulnerability CVE-2018-0296 Trojan PC virus from your computer. However, before you start carrying out the following steps, we advise you to bookmark this webpage and have it opened on a separate device nearby (a smartphone,a tablet, another PC, etc.) as some of the steps might require a re-start of the computer.
Step 1: Safe Mode and Hidden files and folders
In order to increase your chances for success, you are advised to boot your PC into Safe Mode and to also reveal the hidden files and folders that are on it. If you don’t know how to do that, here are links to separate guides that can help you: Safe Mode Guide; Hidden Files and Folders Guide.
Step 2: Task Manager
Use the Ctrl+Shift+Esc or the Ctrl+Alt+Delete keyboard combinations to evoke the Task Manager. Now, go to the Processes tab and look for anything that has the Cisco router, vulnerability CVE-2018-0296 Trojan name on it. If there’s nothing with that name, look for any processes that use too much RAM, have weird or no description and that generally seem suspicious.
If you find anything, right-click on it and select Open File Location. If you are sure that the process was malicious, delete everything in the file location directory. Then go back to the Task Manager Processes tab and stop the shady process by right-clicking on it and then selecting End Process.

Step 3: Startup
Use the Winkey+R key-combo to evoke Run. In the newly-opened search bar type msconfig and hit the Enter button.

In the new window go to the Startup and look through the startup programs. If you see anything that looks suspicious (for example, has unknown or no manufacturer), remove the tick from its checkbox to disable it on startup and then select OK.

[add_forth_banner]
Step 4: Localhost
Type notepad in the Start Menu search bar and open Notepad. Click on File and then on Open. Go to the following folder c:\windows\system32\drivers\etc and open the Hosts file. If nothing appears when you get to the etc folder that can be opened, change the file type from Text documents to All files.

Now look at the bottom of the notepad file and see where it says Localhost. Take a look below that and see if there are any IP addresses there. If there are some IP’s, copy them and send them to us in the comments section down below so that we can determine if they need to be removed.
Step 5: Registry Editor
Re-open Run and type regedit. Hit Enter and once the new window opens, press Ctrl+F. In the search bar, type the name of the virus and click on Find Next. See if anything gets found under the name of the virus and delete the registry keys and folders that come up as results.

However, remember that if you delete the wrong registry key, it might do more harm than good to your PC so if you aren’t sure, you’d better ask us in the comments below about what to do if you find anything inside the Registry Editor.
Step 6: Potentially hazardous data
Open the Start Menu and copy-paste each one of the following locations, one after the other and hit Enter after each so that the folder opens:
- %AppData%
- %LocalAppData%
- %ProgramData%
- %WinDir%
- %Temp%
Open each folder location and sort the files by date (from newest to oldest). Now, delete the ones that have been created around and after the time your PC got infected. In the Temp folder, delete everything.

Did we help you remove Cisco router, vulnerability CVE-2018-0296 Trojan? You need help with any of the steps or you simply want to give us your feedback? Feel free to leave us a comment down below – we highly value the communication with the readers of our content!
Leave a Reply