About the Access Virus
In the following couple of paragraphs, our readers will find valuable information about a malicious software program named the Access Virus. The malware category under which Access falls is the dangerous Ransomware – a very sneaky and malicious type of software that utilizes file encryption as a way to render the user’s personal files inaccessible. When the malicious software is done encrypting your data, it typically generates a ransom-demanding pop-up message that contains instructions from the hackers who stay behind the infection. The Ransomware message normally contains concrete guidelines regarding how to make a money transfer to the cyber-criminal as a form of a ransom. The victim has to pay the demanded ransom as the hackers threaten they won’t make the encrypted files accessible again unless they don’t obtain the ransom money.
In case you’re one of the unlucky victims who have had their computer system infiltrated by Access, you should definitely read the rest of this post plus our Ransomware removal guide manual that you can find below. Before you give a try to any alternative steps, however, first of all, you should understand the fact that a typical Ransomware cryptovirus like Ndarod, Bopador will not function in any way similar to most traditional malware kinds (such as Trojans) which makes it harder to deal with. Things aren’t made any easier by the fact that the most popular means of PC defense, for example, antivirus programs or the system Firewall, do not seem really useful in the battle against the Ransomware threats. Almost all anti-virus programs that people might have on their systems tend to be unsuccessful when facing this malware because, normally, Ransomware infections do not really damage a single thing on the computer. Alas, because of this, more often than not, nothing potentially unwanted gets detected by your safety software. To be completely precise, the method of encryption is not really threatening on its own – it might simply block the access to the targeted files to those who don’t have the corresponding decryption key, but it cannot lead to any harm to the files.
What to do with .access files?
The problem is that when you get attacked by a threat like Access, the only person who is going to possess the key will be the hacker who is attempting to blackmail you. Opting for the ransom transfer, however, is normally thought to be a really bad alternative which not only does not give guarantee about the recovery of your files but also is a direct sponsorship to the hackers’ criminal practice. Furthermore, there are examples of users that have paid the requested money but have, nonetheless, been denied access to their encrypted data files. Some of them have never heard from the hackers and have never received the promised decryption key while others have received keys that simply don’t work and have failed to reverse the applied encryption. That’s why below we have added one specially designed Guide that could potentially assist you in dealing with Access. How successful the manual will be in your case depends on a number of variables, however, it is most definitely worth giving it a go.
SUMMARY:
| Name | Access |
| Type | Ransomware |
| Danger Level | High (Ransomware is by far the worst threat you can encounter) |
| Symptoms | Very few and unnoticeable ones before the ransom notification comes up. |
| Distribution Method | From fake ads and fake system requests to spam emails and contagious web pages. |
Access Ransomware Removal
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to Access
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.
If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the Access.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:
If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and Access , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – Access
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to Access Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
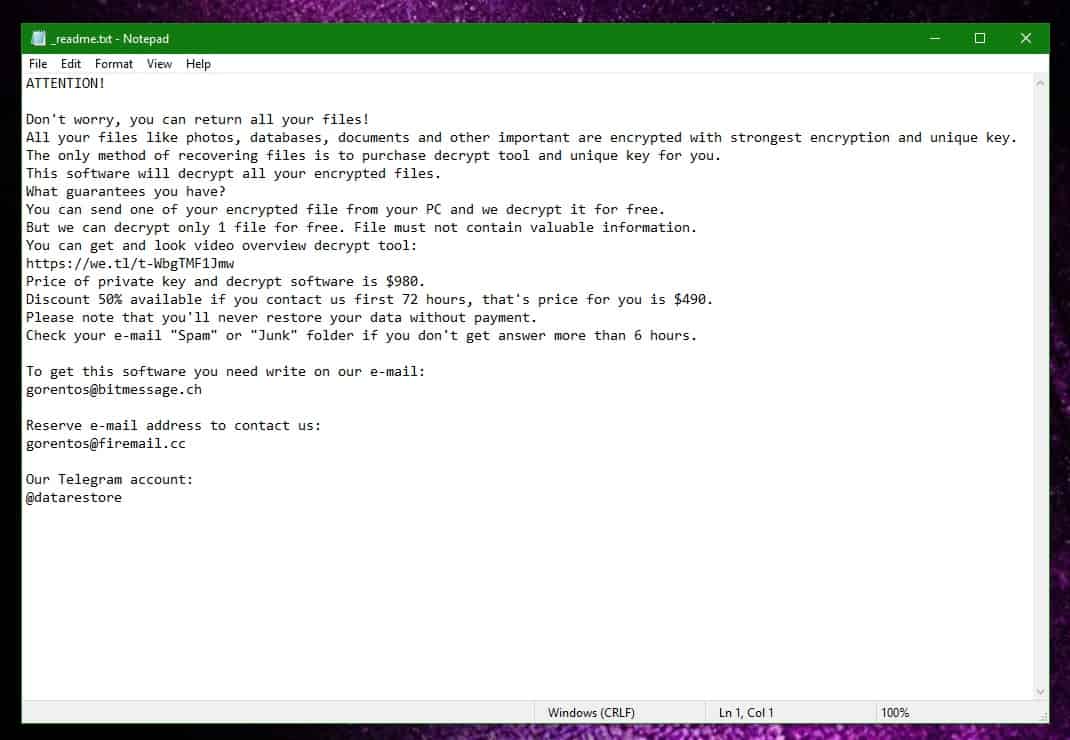
7: Access Decryption
The previous steps were all aimed at removing the Access Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them. For that, we have a separate article with detailed instructions on what you have to do in order to unlock your data. Here is a link to that guide.