Ransomware Decryption Guide
Within this guide, we will attempt to help those of our readers who have had the misfortune of having their PC infected and their files locked by a Ransomware virus. The instructions below will guide you through several methods that can potentially enable you to decrypt any files that have been locked by a Ransomware virus.
However, you must bear in mind that there is a huge number of Ransomware viruses out there – this current guide might help you unlock files that have been encrypted by some of them while failing to recover data that has been taken hostage by others. We cannot guarantee you that even if you go through with the guide, your computer files would certainly get unlocked. That said, it is still strongly recommended that you try out the instructions on this page and only if the do not work for you, consider taking another course of action.
Identifying the Ransomware
Before you go any further with your files’ decryption, you must first make sure that you actually know what the exact Ransomware that has encrypted your data is. There are couple of ways to identify the virus.
Inspect the ransom note
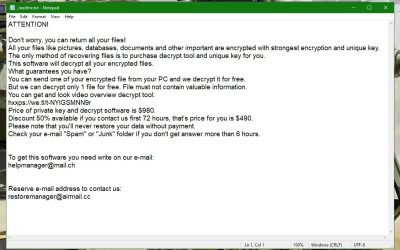
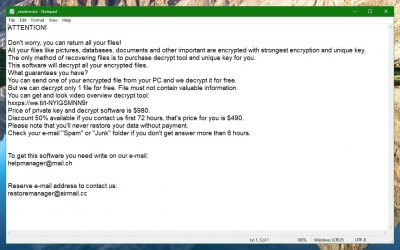
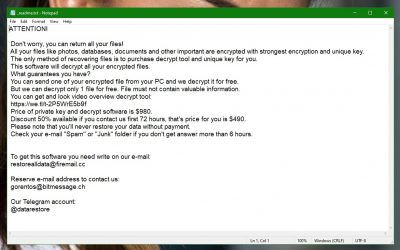
The first and easiest way to find out the name of the Ransomware is to simply read the ransom-demanding note that it has most likely left on your PC. Depending on which Ransomware you might be dealing with, the note might get displayed as a banner on your screen or the virus might generate a notepad file on your desktop or in some other directory. Regardless of the how the ransom note is presented to you, within it, there should be information about the virus and maybe its name will also be written in it. Therefore, check the note and see if you can learn the malware’s name that way.
Use ID Ransomware
If you are struggling to learn the name of the Ransomware that has infected your PC, you can use a free online tool called ID Ransomware. Visit this page to access the tool. Once you go to ID Ransomware, you will have to upload the ransom note file that the virus has left behind as well as a sample of an encrypted file. If there is no ransom note, there’s a field where you can add other information about the virus such as e-mail or IP addresses that the Ransomware has provided you with. Once you’ve uploaded and filled in all the required info, the online tool will identify the virus if it is present within its library.
Warning! – Before you go any further, you must have made sure that the actual malware virus has been removed from your system so that it won’t be able to re-encrypt any files that you might get unlocked, if the virus hasn’t been removed yet, any files that you might decrypt could get locked once again by it. Also, we strongly advise you to make back-up copies of your files and upload then to a separate device (preferably, not another PC or a smartphone but a flash drive for example). Some Ransomware viruses threaten to delete the locked-up data if you attempt to decrypt it without paying which is why it is important to have it backed-up.
Shadow Clone Restore
The first method that we advise you to try against a Ransomware encryption is restoring your data through shadow copies. When the virus encrypts your data, it first deletes the original files and replaces them with identical copies that are encrypted. However, the deleted originals might still be recovered if you are lucky. The tool we will show you here may potentially be able to do that.
- Go to this link to download Data Recovery Pro – a free shadow copy restoration tool.
- Install the program and run it.
- Choose a scan option. We advise you to do a full scan for best results and also have the scan done for all files.
- Once the scanning is finished (Full scan can take a while, be patient), look through the list of files and choose the ones that you want to recover.
Using decryptor tools
There are many decryptors for Ransowmare out there. Here, we will try to keep you updated regarding any such tools that we learn about. However, note that most newer forms of Ransomware do not yet have a decryptor developed for them. That said, if you are lucky, the following list of decryption programs might include a tool that will be able to unlock your files. We will provide download links for the tools that we post here so that you can directly download the one that you might need and put into use.
Trend Micro Decryptor Tool (Free)
This software tool developed by Trend Micro can decipher the encryptions of a number of Ransomware viruses. Also, every now and then it receives updates with new Ransomware viruses that it can decrypt. You can download the Trend Micro Decryptor tool from here.
Here is also a list of the viruses that this decryptor can currently deal handle
- CryptXXX V1, V2, V3
- CryptXXX V4, V5
- TeslaCrypt V1
- TeslaCrypt V2
- TeslaCrypt V3
- TeslaCrypt V4
- SNSLocker
- AutoLocky
- BadBlock
- 777
- XORIST
- XORBAT
- CERBER V1
- Stampado
- Nemucod
- Chimera
- LECHIFFRE
- MirCop
- Jigsaw
- Globe/Purge
- DXXD
- Teamxrat/Xpan
- Crysis
- TeleCrypt
Emisoft Decryptors (Free)
Another security company that offers a significant number of decryption options is Emisoft. They have created separate decryptor tools for a big number of Ransomware viruses and are also developing new ones. You can visit their site and download the decryptor that you need from this link.
Here are some of the Ransomware versions that Emisoft has covered and created decryptors for:
- NumecodAES
- Amnesia
- Amnesia2
- Cry128
- Cry9
- Damage
- CryptON
- MrCr
- Malboro
- Globe3
- OpenToYou
and others…
Decryptor for Petya (Free)
The Petya Ransomware works differently from most other similar viruses. It directly blocks the access to your PC making you unable to boot into Windows until you make the demanded payment. Here, unlocking your PC is trickier than simply decrypting a couple of files.
First, you’d need to unplug your PC’s HDD and plug it in inside another PC. The other machine should have a reliable antivirus on it just in case. Next, download this Petya Sector Extractor (developed by Wosar) and run it – it will extract the necessary data which you will need to fill in on this page. After submitting the required data, you will receive a code that you must write down on paper or on another device. Put the Hard-Disk back into your PC and once the Petya screen appears, fill in the code that you received.
.locked decryptor (Rakhni Ransomware) (Free)
In order to decrypt files locked by Rakhni (ads the .locked extension to your files after encryption), use this link to download the decryptor and to unlock your data.
Note to readers
So far, those are the relevant Ransoware decryptors and decryptor developers that we have been able to find. We will make sure to keep this article updated with any new entries that we come across. Unfortunately, there are still many nasty Ransomware viruses out there that still don’t have a decryptor or some other method that would allow victims to deal with them. Security experts are trying really hard to come up with solutions for newer versions of this noxious malware type but hackers still seem to be a couple of steps ahead. Therefore, always remember that it is simply better to stay safe and not fall prey to such malicious viruses rather than having to deal with what they’ve done with your files or PC.
Last but not least, if you have a suggestion for a decryptor that we missed or are seeking information about a Ransomware virus that wasn’t mentioned here, be sure to hit us up in the comment section and we will make sure to answer your request the best way we can.

Anyone have a decryptor for .arrow as yet?
So far there is no news of such existing yet. We will keep you posted if we find one.
Is there a decryptor for .CRAB files?
Not at the moment.
is there any news about this virus ??
Any notice about
[[email protected]].java
????
any decryptor for crab files already?
Is there any decryptor for .datawait files?
The Ransomware came out two days ago. We will keep you posted if we find a decryptor.
please do notify ASAP you decrypt it. most of my important data has been encrypted
We surely will !!
[email protected]
Thanks
is there any decryptor for .PPTX
Not yet unfortunately. We are on the look out for if any related .PPTX ransomware descriptors show up.
Por favor estou desesperada tambem atras dessa solucao pra decriptar o .pptx
Could you please write in English, sorry for the inconvenience.
I have the the same problem with .PPTX
We are on the look out. As soon as we find one we will post it here.
I have been affected by .DATAWAIT ransomware as well and was wondering whether a solution has been found for decrypting these.
Hi Anthony
We are watching closely for one.
how long could it take to find decryptor for .PPTX
Hi Usuk
Sometimes it takes days, unfortunately sometimes it takes months.
Please add me to the list also I in sinking water with this one.
will do.
Please help, the .PPTX has taken over my life. It has encrypted everything and dropbox even synced the encrypted files to overwrite all the files on my other devices. I cried.
Hi Olusegun
It is very unfortunate to hear this. We are on the look out for a decryptor. Check if there is any options to role back your dropbox account.
Any decryptors for .GAMMA ramsomware?
We just recheck to see if we could find one, but unfortunately still nothing.
i just have this .pptx . any help for this?
As of this moment there is no decryptor.
Hello
Is there a decryptor for Adobe ([email protected])?
Thanks
Unfortunately not yet.
any decryptor for infowait files?
The Ransomware came out 2 days ago. It could take some time until one comes out.
is there any decryptor for .PUMAX
Sorry, nothing yet.
Any solution for .pumax malware it infected my pc.
None at the moment.
Is there any decryptor for .pumax files?
Nothing so far.
Hi, is there any decryptor for .pumax files? Thanks
Still nothing
any decryptor for pumax files?
We are on the look out.
Any decryptors for .PUMAX? please
It just cam out. It will probably take some time.
any chance with pumax ?
We are searching to find one.
Hoping for best. Pumax 🙁
My external hdd inflicted with pumax ransomware. And my important file were there. Hopefully there will be any chance i can save my file. Please help us. 🙁
Hey. Do you have any decryptor for STOP Ransomware?
PLEASE SIR ADD DECRYPTER FOR .PPTX . PLEASEEEEEEE…….
any software for .pumax plz
Hi there, I was also infected with this virus, it sneakily pretended ti be a windows updater and normaly i would leave this running however it got to 98% and got stuck… I assume is was encrpyting the files in that time and whats worse it jumped to my external HDD.. I seem to be facing some time waiting for a decrytptor and I feel sick in the stomach that I would normally have things backed up. I’ve lost about 3 years worth of precious photos of travel aswell as my graphic arts etc, again which I do have some backups of but not as important as my traveling images, I hope you guys can create a decryptor. Thankyou and goodluck to those who read this.
.pumax
Nothing let, let us know if you would like to be added to the notification list for new decryptors.
.pumax decryptor
Nothing let, let us know if you would like to be added to the notification list for new decryptors.
Any latest news on PUMAX ?
Nothing let, let us know if you would like to be added to the notification list for new decryptors.
Hi there, I also was infected with this virus as it was pretending to be a windows update installer. My file extensions are ,Pumax also and I have used Spyhunter to get rid of the damge it was asuing with running apps in the background etc. What concerns me is my files as they have all become encrypted and it seems the same story for thousands of other PC users. Hopefully a team can build software to decrypt this file format.. Even a Brute key. I have access to 2 of most of the files., one clean and the other infected if you wish to help me out, All the best and goodluck out there people.
All we can do is add you to the notification list and let you know when a decryptor comes out.
i have the same problem with pumax. please help me!!
Would you like us to add you to our notification list?
need help here too
.puma deception tool pls pls pls
Same problem .puma decryption tool pls pls pls
My pc also attacked by .puma pls decryption tool
Any progress with decryptor for pumax? And how much time will it take to find one?
any solution about .pumax…….. plz help me
Good Morning, I need help, please. the files on a client computer are encrypted with the extension [[email protected]] .adobe
Can you help me in any way?
I appreciate your help
Lucília Pereira
Hi Lucília Pereira
We will add you to our notification list.
pumas help
[email protected] these dogs also decrypt my gta5..oooooooooooooooh noooooo
Any decryptor for .nasoh files?
This ransom ware is about to ruin me hard!
.pumas decryption tool ??
pumas??
.pumax decryptor help me
Nothing yet, we are on the look out.
Is there anything for .pumas files?
Is there anything for .pumas files
Pls let me know if there is solution for .PUMAS send me an email [email protected]. Thank you very much
You have been added to our list.
Issue with pumas . need decryptor
We can add you to our email list if you like unless you would like to send a notification to another email.
Same issue with pumas. please help with decryptor
We will add you to our email list.
i want to be notified about pumax decryptor.
You will be added to the list.
yes you added me in this list.
any solution about .pumax
Please add me to the notification list for .pumax decryptor. Thank you in advance
any success to decrypt pumas ?
Nothing yet.
any decrypt of .WRITEME ?? please help me
This ransomware is very new, so far we have no information.
I have this new .writeme ransomware, if anyone knows how to decrypt it, please let me know ASAP
We will add you to the email list.
any updates for .PPTX ??
Unfortunately nothing yet.
I have this new ransomware called .writeme, please I need your help ASAP.
Regards
so what decryptor should I use for writeme
My PC has also infected with .writeme ransomware. Please help if any one find the decryptor.
All we can do is add you to our email list.
[email protected]
Thank you, you have been added.
Help *.writeme
puma filer prøv at slette puma sidst i fil navnet virker her
Could you write in English please.
Hola tendran algun descifrador para .djvuu porfavor
Dears my files are encrypted by .djvuu ccould anyone has any decryptor for this fucking virus!?
I have the same problem and i dont find any solution.
Please any remedy to the ransomware djvuq? Can’t still make use of my computer even after removing all traces of the malware.
Is there a decryptor for .djvur?
can .djvuu be fixed??
Thank you for BIG effort. I need a decryptor for .udjvu (not .djvu) ASAP
Any decryptor for .udjvu ?
Decryptor for .udjvu PLS?
decrypter for .djvuu please!!!!!!
hi, add me to the list, I need any notifications for * .djvuu, my e-mail: [email protected]
Dear my files are encrypted by. Udjvu please give me the decrypter please
pls I need help with this fucking virus to pls help me
infected with DJVUQ file ransomware.any decryptor available?
Is there decrypter for. Djvuq filed
please anyone can help me with virus .djvuq?
Is there any solution for .djvuq ?
Any solution for .djvuq yet?
Hello. Any decryptors for .djvuq? Thanks.
Please any decryptor for .djvuq ransomware? My system got infected through a fake windows update some days back. Please help out.
i have got a .djvuq do you know how to get rid of it and get my files back as some of them are need for my disable son .
Hi Sir, Any decryptors for .Udjvu? please
As well, add me to notification list for new decryptor: [email protected]
.writeme infection. Please notify when decryptor found. Thanks
My Pc has been infected with .udjvu Randsamoware.
Does anyone have a decryptor for .udjvu ?
Thanks.
Hello
I have the virus udjvu whit the message _openme. is there some decrytor for. Its on a partion on the harddisk and i can,t goin there. Data recovery can find the files but how do i get whrit of that virus.
cor van gerven
Can you help me with de uudjvu ramsomware. please
my pc files
incfected with .djvuu and .nano
any decryptor
Daniel, decryptor for .djvur? please
.djvur?
OK–i get .djvur files every where with _openme text file—-can i decrypt them????
My PC was infected with .writeme last December 13, 2018. I have tried what where posted “how to” but to no avail. I am trying to recover my files using Stellar Recovery. Am planning to reset my C drive since my audio malfunctioned.
James Bautista
Philippines
Any Descryptor for .DJVUR?
is there a
decryptorr for djvur
Sir my whole data is encrypted. all the files are with .djvuq expansion. plz help
Decrytor for djvur please?
same Issiue .djvur How can i escape ?
Dear
Do you have any available decryptor for “.DJVUR” ransomware.
Please share details for the same.
thanks in advance
Dear
Do you have any available decryptor for “.DJVUR” ransomware.
Please share details for the same.
thanks
Sir any solution for DJVUT??
please I am in horrible situation I need solution for it.
please email me at [email protected]
I’m hit with djuvut. All my files have a djvut extension. Please help me fix this. I promise to be more careful with my internet use. I never thought of all the 8billion plus people on earth I could ever be a victim of this. I’ve waited to wake up from this dream for 18 hours now and now I know it’s real. Please help
Moses Jonathan Kyungai.
is there any solution for .phobos files?
Hi, can you please help me. My files are infected with .djvur
.djvur victim here! I got the virus at jan 5. My av software crashed during update and left me unprotected. After a few hours and restarts i made the pc stable enough to find that i lost about a month of work (i do backup once a month) I really hope that there will be a decrypter!
is there decryptor for DJVUT?
djvut decrypt please
anything for masok dycrptor
most of the file in my pc got infected with .masok. any advised for this .masok virus/ransomware ?
p.s.
i don’t know why, but it look weird, most everything my files is got infected, except my files that i save in desktop is not infected.
Any decryption software for .lapoi???
Please decrypt .MTOGAS ????
Any decryptor for .coharos?
is any decrypt tool for .nacro create
Is there any decryptor for .nasoh?
Plz slove my problem my PC encrypt from .cocars plz give any ideas
Decrypt tool for .coharos
Need help to decrypt .coharos
any decryptor for *.LONDEC
All my files have been infected by versato virus. How do I remove and recover? Thanks
My files are encrypted with .carote ransomware. Is there any decryptor for this? I am a very poor man and cannot pay ransomware.
Anyone having decryptor tool for .NACRO?
This is probably a dead thread but not sure what else to do. Looking for a decrypter for the .adame file extension. anyone know if there is one yet or should I just take a loss here
Good day, my ( repl virus appears to be an online ID, decryption ) need help