[add_top_banner]
.Npph
.Npph belongs to the computer virus category of ransomware. This means that .Npph performs a certain malicious act on victim computers and then demands that the victims pay ‘ransom’ in order to have the effects of it reversed.
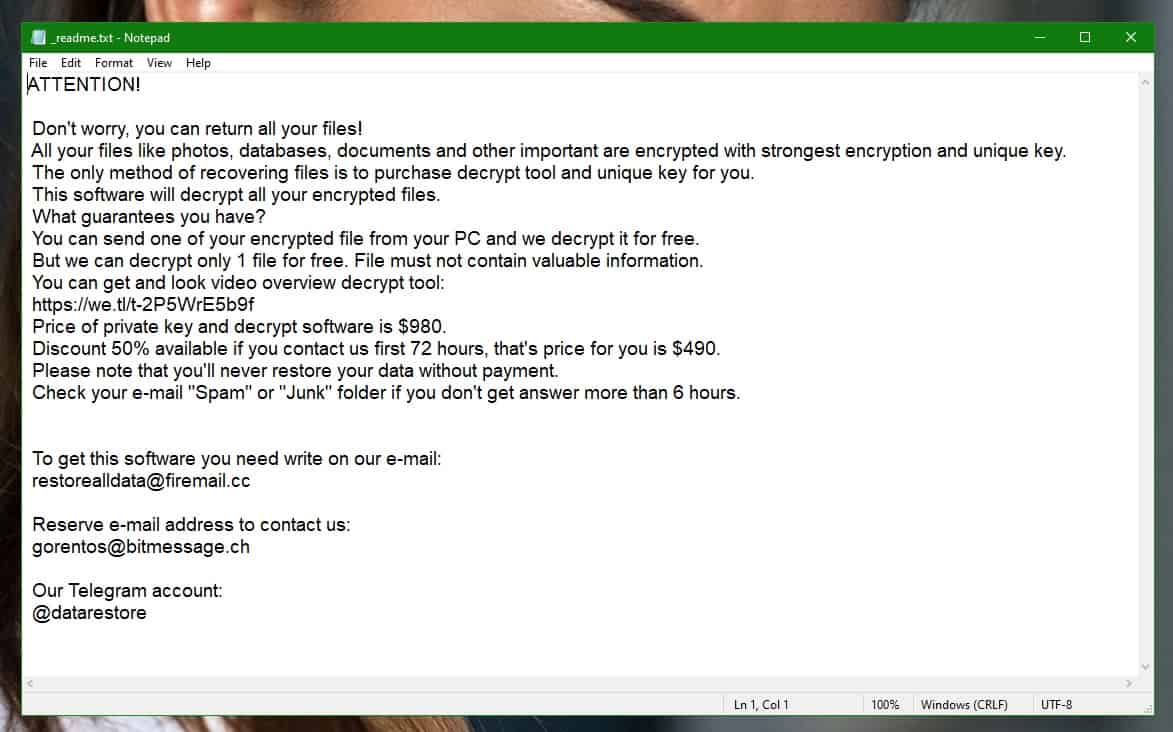
This is a classic blackmail scheme, and in this form it originated in the early 90s, but it wasn’t until the past decade or so that ransomware really started experiencing its hay day. .Npph, specifically, targets users’ files and places a complex encryption on them, which prevents anyone from being able to open them. Then, it proceeds to blackmail the owners of said files for money, promising to restore the files to their original state only after the demanded amount has been paid.
If this is what has happened to you, then we recommend you read through the following post and stick around for the removal guide that comes after. We do not recommend rushing to pay the ransom, as it will only encourage the criminals behind .Npph to continue on with their malicious scheme. And on the other hand, there’s really no guarantee that they will in fact send you the decryption key necessary to recover your data. Instead, we recommend first removing the ransomware from your system and then attempting to retrieve your valuable files through other means, which we have also listed below.
The .Npph virus
The .Npph virus acts in complete stealth, which is why most often it doesn’t trigger even the best security software. The makes the .Npph virus and others like it exceptionally dangerous.

In rare cases when the infected computer doesn’t happen to have a lot of processing power and it has a very substantial number of different files stored on it, a ransomware infection like this may cause an overall system slowdown. And this may prompt a perceptive enough user to have a look at their Task Manager to see what might be causing the problem. In this case, you would see the ransomware operating at the very top of the list as the process consuming the most system resources. And should this ever actually occur, you must immediately shut down your system and don’t attempt to switch it back on before you’ve contacted a specialist.
The .Npph file extension
You’ll notice that all the encrypted files on your computer end with the .Npph file extension. This .Npph file extension essentially makes the files unreadable to any type of existing software and prevents them from being opened.
What’s important to understand here is that encryption in itself is not a harmful process. On the contrary, it’s actually a very helpful one that we rely on every day to keep sensitive information safe from prying eyes online. But obviously it can also be used for evil, and very successfully at that. And due to its complexity, dealing with encryption like that of .Npph can be very difficult. This is to say that you should be prepared to deal with a potential permanent loss of all your data, as even paying the requested ransom may not be enough to save it. Still, do remove .Npph from your PC and check out the file restoration tips that we’ve included, and hopefully you will be able to retrieve at least some of them.
SUMMARY:
| Name | .Npph |
| Type | Ransomware |
| Danger Level | High (.Npph Ransomware encrypts all types of files) |
| Symptoms | .Npph Ransomware is hard to detect and aside from increased use of RAM and CPU, there would barely be any other visible red flags. |
| Distribution Method | Most of the time, Trojans get distributed through spam e-mails and social network messages, malicious ads, shady and pirated downloads, questionable torrents and other similar methods. |
[add_third_banner]
Remove .Npph Ransomware Guide
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to .Npph
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.

If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the .Npph.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:

If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and .Npph , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – .Npph
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to .Npph Ransomware. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.
7: .Npph Decryption
The previous steps were all aimed at removing the .Npph Ransomware from your PC. However, in order to regain access to your files, you will also need to decrypt them or restore them. For that, we have a separate article with detailed instructions on what you have to do in order to unlock your data. Here is a link to that guide.