About the Recorded You Email
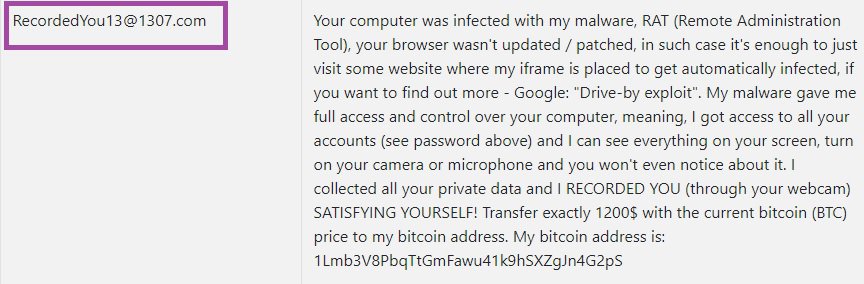
We understand that it can be both frustrating and anxiety-inducing if you learn that a Trojan such as the insidious Recorded You has entered your personal or work computer and is currently residing in it. However, the fact that you are aware of the malware’s presence in the machine is good news, really. Most Trojans are rather difficult to notice – something that’s especially true for newer threats like Recorded You, “Drive by exploit”, 1nCuB0. A good antivirus may keep you safe from Trojans that are already in its database but new infection like the one we are focusing on right now are likely to slip past the security tools that most users may have because the protection software may be unable to recognize the new threat as it is has not yet been added to its malware definitions. This is, in fact, why it is important to have antivirus and/or anti-malware programs that get daily updates and that have some form of heuristic protection – a feature that can help with the detection of threats that are not in the security tool’s database yet.
Anyway, the main topic of this post is Recorded You, and if this is indeed the malware piece you are presently dealing with, let us tell you a bit more about the potential harm that you may face if you don’t remove the infection on time.
Trojan Horse versatility – why they can be so unpredictable
The goal of a given Trojan Horse infection may oftentimes remain a mystery to the users that have been attacked – at least until the effects of the infection become obvious. This is because a Trojan is a tool for cyber crimes that may possess great versatility. It can be used for personal espionage, for online banking thefts, for the distribution of other threatening programs like Ransomware, for stealing sensitive data from the attacked machine, and many, many more.
Once a virus of this type enters the computer of its victim, it typically needs to gain Admin rights in order to have access and control over the whole system. To achieve this, however, the Trojan typically needs its victim to make a mistake. Typically, this mistake comprises the interaction with the Trojan itself – the execution of the file that carries it. This is why most Trojans are disguised when they first get introduced into the computer – disguised as the installer of some cool game or some expensive program (that is now free), or as some other piece of data, which the user may be tempted to interact with. Typically, pirate sites are known for spreading such pieces of data, which could be potential carriers of Trojans like Recorded You. However, there are other distribution methods for Trojans – spam messages, misleading web ads, clickbait banners, and so on and so forth. And, as we said, even a good antivirus may not always be able to detect all potential threats, which is why you really need to look out for yourself while on the Internet. As for the removal of Recorded You, follow the instructions below and you should be able to take care of this threat.
SUMMARY:
| Name | Recorded You |
| Type | Trojan |
| Danger Level | High (Trojans are often used as a backdoor for Ransomware) |
| Symptoms | A Trojan Horse infection could cause various types of disturbance in your system – crashes, BSOD, errors, freezes and more. |
| Distribution Method | Typically, the Trojans are disguised as the installer for some illegally downloaded game or some other pirated program. |
Remove Recorded You Email
1: Preparations
Note: Before you go any further, we advise you to bookmark this page or have it open on a separate device such as your smartphone or another PC. Some of the steps might require you to exit your browser on this PC.
2: Task Manager
Press Ctrl + Shift + Esc to enter the Task Manager. Go to the Tab labeled Processes (Details for Win 8/10). Carefully look through the list of processes that are currently active on you PC.
If any of them seems shady, consumes too much RAM/CPU or has some strange description or no description at all, right-click on it, select Open File Location and delete everything there.
Also, even if you do not delete the files, be sure to stop the process by right-clicking on it and selecting End Process.
3: IP related to Recorded You
Go to c:\windows\system32\drivers\etc\hosts. Open the hosts file with notepad.
Find where it says Localhost and take a look below that.
If you see any IP addresses there (below Localhost) send them to us here, in the comments since they might be coming from the Recorded You.
[add_forth_banner]
4: Disable Startup programs
Re-open the Start Menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab. If you are on Win 10, it will send you to the Startup part of the task manager instead, as in the picture:
If you see any sketchy/shady looking entries in the list with an unknown manufacturer or a manufacturer name that looks suspicious as there could be a link between them and Recorded You , disable those programs and select OK.
5: Registry Editor
Press Windows key + R and in the resulting window type regedit.
Now, press Ctrl + F and type the name of the virus.
Delete everything that gets found. If you are not sure about whether to delete something, do not hesitate to ask us in the comments. Keep in mind that if you delete the wrong thing, you might cause all sorts of issues to your PC.
6: Deleting potentially malicious data – Recorded You
Type each of the following locations in the Windows search box and hit enter to open the locations:
%AppData%
%LocalAppData%
%ProgramData%
%WinDir%
%Temp%
Delete everything you see in Temp linked to Recorded You Email. About the other folders, sort their contents by date and delete only the most recent entries. As always, if you are not sure about something, write to us in the comment section.